ICTTEN622 Produce ICT Network Architecture Designs Assignment
- Subject Code :
ICTTEN622
- Country :
Australia
Topic 1: Preparing an ICT network architecture design
Welcome to this unit about producing ICT network architecture designs based on a clients specifications.
Modern businesses are dependent on an effective network system in order to be able to conduct their operations efficiently and to communicate within, as well as outside the organisation with a range of stakeholders such as customers and suppliers. Therefore the ICT network architecture needs to be designed to operate as effectively and securely as possible.
As someone responsible for designing a network you will need to take a range of business considerations into account such as business growth (or even downsizing), network security and compliance requirements and new technologies such as mobile devices, virtualisation and cloud security.
In this first topic we look at some key concepts in relation to ICT network architecture design and activities that need to be completed in preparation for producing an ICT network architecture design.
Introduction to network design
Generally speaking, ICT network architecture relates to hardware, software, access and protocols and the overall design of an IT system including logical and physical interrelationships between its components.
Network architecture design is the planning phase for a business ICT architecture (also referred to as infrastructure or system) to ensure that the network works efficiently.
An ICT network architecture design generally includes:
- a map of the network
- details of the cabling required
- the number, type and location of all network devices
- the IP addressing structure
- details of the network security architecture and processes.
Network technologies
It is important to understand key concepts as relevant to designing network architecture. These can be thought of as technologies.
Review all of the information in the table below about technologies and principles behind these technologies.
| Technologies | Key Principles |
|---|---|
| Access networks | An access network is a user network that connects users to a service provider and through the carrier network to other networks, for example, the Internet. Types of access networks include:
|
| Core networks | Core networks are a core part of a telecommunication network that provide a range of services to customers connected by the access network. The key function of core networks is to direct telephone calls over the public-switched telephone network. Core networks have a number of functionalities including:
|
| Network topologies | network is called network topology and is also referred to as network architecture. It is essentially the structure of the network. There are several main types of network topologies, including point-to point, bus, star, ring, mesh, tree and hybrid. Read more about different types of network topologies at: https://www.webopedia.com/quick_ref/topologies.asp |
| Mobile cellular networks | A mobile cellular network is wireless and the network is distributed over land areas called cells and with each cell or a number of cells served by a fixed location transceiver. Through this the network transmits voice, data, and other content. Coverage is enabled over a wide geographic area and allows devices such as phone and laptops to communicate with each other through the fixed transceiver and associated telephone networks. |
| Network protocols and operating Systems | A network protocol defines rules and conventions for communication between network devices. For network protocols to operate, an operating system that implements the protocols runs on every node. |
| Optical networks and principles | Optical networks are data communication networks that are built with optical fibre technology. Optical networks use optical fibre cables to convert data, as well as pass data as light pulses between sender and receiver nodes. |
| Radio frequency (RF) technologies and principles | Radio frequency refers to the frequency band at which wireless telecommunications signals are being transmitted and broadcast. |
| Radio frequency identification (RFID) hardware and software | Radio Frequency Identification (RFID) is a technology that allows any object to be wirelessly identified using data transmitted via radio waves. An example of RFID hardware is an antenna, which transmits and receives signals. An RFID software is used to process data sent to and received from RFID devices and there are many different types of RFID software. |
Work details, specifications and scope
Now that you understand principles of technologies as relevant to designing ICT network architectures, lets go back to the process that you will need to follow to prepare to produce your design.
In order to be able to design the ICT network architecture, you will need to have information about the clients requirements.
Details of the requirements can be at both a strategic and operational level. At a strategic level the client may provide you with information about the overall objectives for the business , expansion plans and so on which influence the ICT network required.
At an operational level you would need to find out information such as work details, specifications and the overall scope of the project.
The work details that you obtain would generally be directly from the client and include their specific requirements. You may receive a general request to design a network for adequate coverage for all users. However, you will need much more detail than this. This could require meeting with the client and finding out information that will help you understand their needs and expectations. For example:
- The scope (the scope of the project should be defined in a scope of works or project scope description which will include everything that is included within the boundaries of the project)
- Objectives of the work e.g. improve efficiency of the network
- Current issues e.g. problems or opportunities that a new network design will create
- The budget or estimated costs
- A deadline or schedule for completion
- Physical characteristics of the site and current network infrastructure in place
- The amount of voice and video traffic
- The budget or estimated costs
- Devices, apps and programs that will use the network
- Client expectations
Part of the work detail will also be to obtain details of network layout and parameters; it will provide a visual picture of the IT environment that can be used to make decisions for modifications upgrades or expansions.
A network summary and/or network diagram should identify all the elements of an ICT infrastructure, including the network layout. It can cover:
- the type of network topology, the size of the area it covers, if there are multiple LANS connected
- devices on the network such as switches, servers, firewalls, routers and workstations
- network addressing for IP address ranges and subnet masks
- network services, DHCP and DNS server addresses and ranges
- Quality of Service (QoS)
- high level routing
- links to relevant procedures
- L1/L2 drawings showing physical connectivity and layout of the network
- parameters of the network.
Determining the desktop applications and operating systems used is also important information to access. For example, the network performance monitoring software, spreadsheets for recording information, project management software such as Visio and technical specifications of an operating system such as CPU performance, storage capacity and memory speeds.
Remember that:
- An operating system is the most important software on a computer and manages the computers memory and processes, as well as all software and hardware. Typical operating systems are Windows, Mac and Linux.
- A desktop application is a standalone application on a computer. A common desktop application is software such as Microsoft Office and web browsers such as Chrome.
Activity: Research and discuss
Work in small groups and outline the desktop applications and operating system being used in your classroom or at the closest ICT lab or facility.
Discuss your findings with your group.
Activity: Research and discuss
An example problem statement:
The organisation has connectivity and performance issues, creating issues with production and disengaged employees.
- What further information would you need to ask the client to gain a full understanding of their requirements?
Discuss this statement with your group.
Site access
As part of the network design process you may need to visit a clients site. The following table outlines some of the compliance requirements that can be involved when undertaking a site survey, requiring access to a clients premises. Note that this can change depending upon the industry, organisation, location of premises and other f actors that can be related to the specific site survey
| Compliance | Requirements |
|---|---|
| Security | Entry such as passcodes, locks, advanced entry requirements (for example it may include workplace health and safety requirements relating to pandemic/virus compliances). It could also include, signing in procedures, permission forms, codes for different security access locations and access codes for computer networks and equipment. |
| Codes of practice | Following a code of practice on professional conduct such as the Australian Computer Society Code of Professional Conduct to ensure that you always display professional conduct. Codes of practice relating to workplace health and safety (such as working in confined spaces or first aid in the workplace). |
It is important to be able to identify and follow all relevant legislation, codes, regulations and standards that apply to your work including worker obligations to compliances as well as those followed by the organization that you work with or when attending onsite work at a site. Lets look at some of these in the table below.
| Legislation, codes, regulations, standards | Description |
|---|---|
| Workplace Health and Safety Act 2011 | Includes security arrangements for accessing site, safety with regard to electrical equipment, manual handling and safety of workers as well as following organisational policies and procedures for workplace health and safety. |
| Workplace Health and Safety Regulations 2021 | Includes specific requirements for particular hazards and risks, for example, noise, machinery, and manual handling. |
| Workplace Health and Safety practices | Work health and safety practices that you follow on site, for example, using PPE such as ear protection if there is excessive noise or ensuring you use correct manual handling techniques or making sure you take regular breaks. |
| Privacy Act 1988 including the privacy principles and notifiable data breach obligations. | Relating to keeping information and data secure, protecting data and information, and obligations for notifiable security breaches.Following organisational policies and procedures relating to privacy, security and confidentiality of data and information and acceptable use of IT devices. Undertaking to protect data such as using backup and data recovery strategies, protecting against malware and virus and network perimeter controls |
| AZ/NZ ISO31000 standard for risk management | AZ/NZ ISO31000 standard for risk management - Risk assessment for undertaking works. |
| ISO 27001 standard for information security management systems | Using codes of practices for information security management and to guide security via integrity, minimising risk, information availability and controls. |
| Competition and Consumer Act 2010 | Anti-competitive conduct and consumer protection provisions. It includes economic regulation of the communications sector for telecommunications, broadcasting, content, and the national broadband network (NBN). |
| Corporations Act 2001 | For exercising due care and diligence to prevent, mitigate, manage or respond to an incident (relating to configuring and testing equipment). |
Reviewing specifications and requirements
Once the specifications and requirements have been obtained from the client then it must be reviewed to identify the type of ICT network and network specifications required.
The ICT network can include hardware and or software such as:
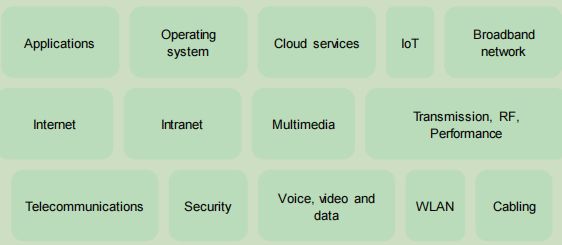
As an example, a client may require a new wireless LAN installed, in which case, there would be specific requirements to design and deploy this service, such as the current ICT infrastructure, building and environment, hardware and software in use, cabling and access po ints, geographical areas, performance requirements, devices used and number of users.
Activity: Read
The following example for the university of York is a requirements document for project managers and contractors for IT services network infrastructure specification: https://www.york.ac.uk/it services/downloads/net/IT Services Network Infrastructure Specificati on.pdf Take any notes to summarise what you have read and keep for future reference.
Consulting with key stakeholders
Consultation with key stakeholders to identify their requirements involves communicating the desired solution, gaining feedback and information to help with the implementation of the solution. Consultation can be with:
- a project team
- the development team
- a sponsor/client
- users
- project manager/supervisor
- department manager
- ICT team.
Conducting consultation can be through: ,/p>
- holding meetings
- distributing questionnaires or surveys
- conducting interviews
- group forums
- focus groups
- presentations
- distribution of documents
- observation.
Consulting with stakeholders can support the development of an ICT network architecture design through providing the necessary information and documentation, along with gaining an understanding of their requirements. Consultation can also improve implementation outcomes and to help control risks.
When consulting with stakeholders, it is important to use effective communication skills to ensure that the project will be a success.
Activity:Read
Top five effective communication skills for project managers. Article: https://www.projectsmart.co.uk/communications-management/top-five communication-skills-for-project-managers.php
Take any notes to summarise what you have read and keep for future reference.
Assessment of business problems, opportunities and objectives
The business problem provides an overview and basis for finding a solution. A business problem could be:
- The quality of Internet service is poor for customers when conducting online shopping from the company website.
- The library ICT infrastructure is not coping with the amount of devices connecting to the network.
- Security threats are a constant issue for our organization.
These statements can be expanded in the requirements report, proposal for tender, client brief or client specifications report.
Different problems can create business opportunities that demand different solutions. Some opportunities can be:
- Problem: The quality of Internet service is poor for customers when conducting online shopping from the company website.
- Opportunity: Create better customer service by upgrading the software/hardware.
- Problem: The library ICT infrastructure is not coping with the amount of devices connecting to the network.
- Opportunity: Create further access points and install repeaters to increase performance.
- Problem: Storage capacity is always at a high level.
- Opportunity: Implement cloud storage options.
A client may have clear objectives such as:
- The network needs to have a higher bandwidth to cope with the amount of network traffic.
- The ICT wireless network must cope with further expansion needs.
- Secure the network from further vulnerabilities.
Activity: Read
Objectives should be SMART! Read this article on SMART project management. Article: https://www.wrike.com/project-management-guide/faq/what-is-smart-in project-management/ Take any notes to summarise what you have read and keep for future reference.
To effectively solve a business problem, a methodology or framework can be used to work through the problem and to meet the objectives.
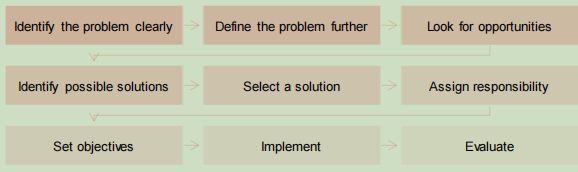
Activity:Read
Read the article below on tools and techniques for problem solving. Article: https://www.educational-business-articles.com/problem-solving-strategies/ Take any notes to summarise what you have read and keep for future reference.
Confirming details with an appropriate person may be through attending a meeting and discussing the outcomes of assessing the business problem, requirements report or proposal brief.
Presenting different options or a draft solution and discussing feedback with a client or appropriate person making decisions may be part of a policy or procedure such as the next step in a project management or ICT project framework.
It may require approval signatures, contract signatures, confirmation to go ahead with the next stage or confirmation that the requirements have been understood and are meeting client objectives.
Topic 2: Producing a preliminary ICT network architecture design
Technical requirements according to specifications
Once a client has confirmed that the requirements have been correctly identified and a solution has been approved, then the next step will be to ascertain the technical requirements, according to the specifications.
The technical requirements will be specific to the client and can relate to a number of networking options such as:
- increasing bandwidth
- addressing hardware problems
- dealing with potential network growth
- identification of a better network security
- addressing network traffic congestions
- acquiring new technologies
- looking at power usage
- addressing software problems
- solving transmission dropouts
- upgrading software or hardware.
The hardware components can include:
- cabling for a new network
- introducing cellular phone network
- internet protocol tv (iptv)
- optic fibre cabling
- switches
- access points
- multimedia.
Software may include:
- operating system software
- performance monitoring
- application software
- network management software
- diagnostic tools.
The network elements needed will be dependent upon the size of the geographical area, the type of building, the environment, network usage, power limitations, compatibility with older standards, legacy systems, network range and distance and building obstructions. It may include:
- add-drop multiplexer
- antennas
- base station
- dense wavelength division multiplexing (DWDM) unit
- encoder
- using a gateway
- installing local area network (LAN) switches
- further routers
- servers
- wireless networks
- RFID equipment
- installing switches, routers RFID
- a protocol analyser.
When undertaking the development of technical requirements for a business:
- focus on the clients requirements
- select the technology needed to best support these needs.
Select software solutions to suit business platform
The selected software solution will be specific to the client and will need to suit their business platform.
The software solution should fit the business requirements and focus on the client needs. It can range from:
It can also include:
- customer satisfaction
- user licence
- training and support
- specific techniques and tools
- methodologies and standards.
The business platform will have an effect as to what software solution can be deplo yed. For example, compatibility with new hardware components, standards, operating system and applications. Upgrades may be required, or depending on the platform it could be integrated or may need replacing.
The options will ensure that the solution will meet client requirements, work with the business platform and meet any budget requirements.
Activity:Read and discuss
Read this brief definition of compatibility. Article: https://whatis.techtarget.com/definition/compatibility Consider why compatibility is important in terms of software solutions for a business. Do some research too to find out some common approaches for resolving compatibility issues.
Make notes on your answers as this will help with your assessment.
Develop preliminary physical network diagrams
A physical network diagram provides a visual representation of the IT environment and can be used to make decisions for modifications upgrades or expansions as well as providing a preface for the architecture blueprint.
A network diagram identifies all the elements of an ICT infrastructure, including the network layout.
It can cover:
- the type of network topology, the size of the area it covers, if there are multiple LANS Connected
- devices on the network such as switches, servers, firewalls, routers and workstations
- network addressing for IP address ranges and subnet masks
- network services, DHCP and DNS server addresses and ranges
- Quality of Service (QoS)
- high level routing
- links to relevant procedures
- L1/L2 drawings showing physical connectivity and layout of the network
- parameters of the network.
The architecture of a computer network may also include:
- the carrier network information, which could contain:
- access
- billing
- type of service, for example, broadband
- data transmission
- optical fibre
- wireless transmission
- configurations:
- large memory model
- requests per second
- small memory model
- database software such as:
- Microsoft SQL server
- MySQL
- oracle
- the operating system such as:
- Linux
- Mac OS
- Novell Netware
- Windows.
Network layout diagrams
Network diagrams can be drawn using software to provide a visual understanding and record of how the network is connected.
Configuration of IP addresses
Its important for you to understand how to configure an IP address on an IP network and why it is important to do this. An IP address uniquely identifies a device on an IP network and an IP addressing plan is vital to ensure there is an effective system in place for allocating, recycling, and documenting IP addresses and subnets in a network.
Activity: Practical
Configure an IP address on an IP network. Your trainer/assessor will provide you with an activity.
Possible impacts of the network design on the business requirements
Produce a document on the possible impact of the network design on the business requirements. Possible impacts may refer to:
- fewer downtimes
- improved efficiency
- improved response times
- increased return on investment
- lower operational costs
- more 'user friendly' network.
Topic 3: Evaluating the preliminary design and likely performance using forecast demands Predict forecast traffic demands and impacts
When planning to change any ICT infrastructure, the current and future demand requirements of the client and their business must be taken into consideration.
Identification of the clients current needs will determine the requirements for the design. Examples of needs can be:
- a reduction in the cost of maintaining multiple networks
- supporting business expansion
- improving the productivity of employees by enhancing and integrating internal communications through mobile devices, without compromising security compliance
- a network that can support voice, data, video and wireless
- capability to support the introduction of remote sites to the network without a redesign
- the ability to provide isolation between traffic of external guests and internal employees, complying to organisational security policies for wired and wireless connection.
The current needs may include the ability to support ten users, however, if there is future expansion then the implications of this would need to be addressed such as:
- future capacity
- performance needs
- connectivity speed
- security
- storage.
Future advancements in technology such as cloud, augmented reality, virtualisation, AI machine learning and the resulting changes to business practices, trends and legislation should also be considered when determining future needs.
An infrastructure that is adaptable and able to cope with future needs and demands can be integrated into the foundations of an IT network and in turn keep pace with business needs.
Traffic forecasting tools can be used to plan and estimate for future traffic based on the projected growth of the current measured or simulated traffic. This can help determine the impact of the new traffic on the network and plan for future demands.
An organisation can use a number of tools and techniques to predict the impact on a network design from both current and future demand requirements. For example:
- A network traffic monitor analyses the network usage of a LAN, providing upload and download statistics. The application monitors and counts the IP traffic between the local area network and the Internet.
- Conducting a LAN speed test for current performance.
- Benchmarking network throughput to test connectivity based on packet sizes.
- Testing the performance of a network either wireless or wired using a throughput test allowing a user to evaluate network performance depending on the quality of service (QoS) settings.
- Radio frequency (RF) tests can detect the presence of unwanted interference that can disrupt signals from wireless devices and determine if CRC and PLCP errors occur due to packet collisions occurring.
- Wi-fi radios to measure Wi-Fi signal strength, noise, co-channel interference, network configuration information and spectrum analysis.
- Spectrum analyser used to detect, locate and analyse interference which is non-WiFi and to validate the health of the RF spectrum by measuring whether wireless channels are busy or free.
- Wireless packet capture tools or packet sniffer is a software program used to intercept frames that are being transmitted by nearby AP or stations. Logged information can be used to analyse and troubleshoot and optimise difficult wireless network issues.
- Signal propagation assessment to predict signal propagation between data points.
Activity: Read
Cisco Visual Networking Index: Forecast and trends 2017-2022 White paper Have a look at this white paper that includes global traffic projections. Article:
https://twiki.cern.ch/twiki/pub/HEPIX/TechwatchNetwork/HtwNetworkDocuments/whit e-paper-c11-741490.pdf
Take any notes to summarise what you have read and keep for future reference.
Benchmark the design using expected performance parameters
Network performance metrics can be used to benchmark the design using expected results or parameters. There are a range of performance parameters that can be used to benchmark the design as explore below:
Measuring latency
For a planned install of voice or an application that relies on real time video transmission, the current performance can predict if this would be possible or if an upgrade is required.
Activity: Read
Measure network latency.
Article: https://au.pcmag.com/it-watch/57995/measure-your-network-latency-before it-becomes-a-problem
Take any notes to summarise what you have read and keep for future reference.
Bandwidth and throughout
To measure the data transferred over a network. This can be used to ascertain the amount being used and how future growth in say number of users or use of the network will be affected.
Uptime
Hardware and software metrics such as CPU utilisation, memory use, remaining hard drive space, using the network monitor to track services and software.
Further performance parameters that can be used to benchmark the design include:
- congestion
- distortion
- interference
- packet loss
- data security
- attenuation
- Bit Error Rate (BER)
- dropouts
- polarisation.
Activity: Read
Use IPconfig on your computer to look at connectivity issues: https://docs.microsoft.com/en-us/windows-server/administration/windows commands/ipconfig
Take any notes to summarise what you have read and keep for future reference.
Activity: Watch
Watch the following videos about security protocols and data encryption techniques . Video: https://www.youtube.com/watch?v=VYRPDmBaGcA (07:58) Video: https://www.youtube.com/watch?v=UJiLgUtddlM (08:31) Consider the security protocols, standards and data encryption techniques used in a small local area network such as a home office network.
Make notes on your answers and discuss your findings as a group
Activity: Group work
You can work in pairs for this activity.
Using the following website, test your own computer for packet loss (use an alternative site or support features to undertake the task if this website is unavailable or not appropriate to your OS):
https://www.netadmintools.com/testing-for-packet-loss-on-windows/
Take a screen shot of the results. Analyse the results and provide a summary.
Submit all work as professionally written documents within the timeframe allocated. Your trainer/assessor will provide your group with feedback.
Review the designs likely performance profile
Once the predicted forecast traffic demands and impacts have been made, along with the benchmarks for expected performance parameters then these should be reviewed to provide a likely performance profile.
Network capacity planning can help to understand some key metrics, such as:
This creates a network profile to help understand the maximum capability of current resources along with the impact of adding further resources needed to support future requirements.
The profile can help to identify additional resources such as hardware or software, as well as additional staff required.
Determine the supplier costs
Determining the costs involved with purchasing supplier products will be dependent on a number of factors:
Choosing the right software and hardware vendor for products and equipment to be purchased, may require evaluation and in some cases testing.
This can be via free trials, research conducted, using pilots and checking reviews and credentials of providers.
Using a checklist or set of criteria can be helpful in choosing the right vendor. For example:
Costs involved can range from purchase of hardware and software, installation of cables, typographical area to be covered, installation fees, etc.
Evaluation of a range of products should be made, comparing costs, compatibility, features, capabilities, quality, shipping fees and supplier support
Evaluation on predicted performance and costs of the network architecture design
Finally, an evaluation report should be written to outline the information gathered on the predicted performance and costs of the network architecture design.
The clients business specifications and business requirements should be addressed in the report with recommendations.
An evaluation report should be professionally written, clearly and lo gically structured and include all the information gathered throughout the evaluation of the network design. It should include:
The report can then be distributed to the key stakeholder, client or decision maker for review, feedback and/approval for the next stage of the project.
Topic 4: Finalising the network design and obtaining approval
Reviewing benchmarks, requirements and final design proposed
The final stage for producing a network architecture design is to begin with a review of the benchmarks, requirements and final design proposed.
This ensures that the most up-to-date information has been obtained and checks can be made on the final design proposed. Any anomalies or variances can be addressed at this point.
Determining support and training
Any changes to the network, including upgrades, new components, systems or installation of further equipment may require support and training for staff and users of the system. The possible impacts for change can have negative consequences on the successful implementation of a project if not addressed before the change is implemented.
This can be looking at:
Change management tools, techniques and processes can be used to support any changes and identify the support and training required.
Activity: Read
Read the best change management tools of 2022.
Article: https://thedigitalprojectmanager.com/change-management-tools/ Read the article below on skills gap analysis.
Article: https://www.cleverism.com/lexicon/skills-gap-analysis/ Take any notes to summarise what you have read and keep for future reference.
Support and training can be varied and will be dependent upon the needs of the users. Some examples are:
What training would each member of the class require if a new WLAN were to be installed?
Discuss your thoughts as a group.
Obtaining the latest technical specifications and pricing
It is important to ensure that the latest technical specifications and pricing has been sourced to ensure the most up-to-date information on hardware and software being purchased.
Any research previously undertaken may have been carried out months previously and feedback, evaluations and reviews may have changed some of the specifications for what should be purchased.
Vendors may be researched using criteria and also may be:
Either way, a list of requirements, estimated pricing and purchasing processes must be obtained and then approved before ordering.
Procedures for contacting vendors can be via proforma invoices, a formal email request, telephone call, online enquiry or specified by the client or organisational policy and procedures.
Activity: Read and discuss
Visit a supplier website and look at the technical specifications for three network components for purchase. What is the process for contacting the vendor? What are the specs and pricing? Now look at another vendor and make a comparison. What sets the two vendors apart? Is it the shipping, time to ship, guarantee/warrantee, price or features of the components?
Discuss your findings with a group
Documenting the network design and presenting documentation
Documenting the network design and presenting the documentation for approval should be done so according to the project management guidelines, organisational requirements/policies and procedures or in a professionally structured format that is clear and easy to understand for the client.
The design of the network can be presented using:
It is important that client clearly understands the choices made for the project. Providing the best possible advice can support the client in making the best possible choice.
Assumptions can be made that the client is not technically able to understand the option presented to them. Therefore, it should be:
Documentation may also include:
The amount of information that must be presented to the client for approval should be clearly and logically presented in a report with supporting documentation such as network diagrams and data analysis results attached.
Obtaining sign off on final business solution
Signing off on a business solution will involve meeting with the client, presenting the designs and gaining approval.
Obtaining feedback from client ensures that the client requirements have been met or adjustments, modifications or questions need to be addressed before the implementation can go ahead.
Feedback can be in the form of a report, a list of questions proposed, a completed feedback form, response to the proposal or an email confirming approval or not.
Once the project has been signed off this may mean a part payment of the project can also go ahead. The approval will commence the next stage of the project and close the design stage.
Sign off may be in the form of:
See the Australian Government Contract Management Guide for an idea of what is contained in a typical contract.
Guide: https://www.finance.gov.au/sites/default/files/2020- 12/Contract Management Guide December 2020 - Master.pdf
Take any notes to summarise what you have read and keep for future reference.
Activity: Rearch and discussion
Source a contract template that could be used for a client to approve an ICT network architecture design.
Discuss your findings with your group.
- List down the performance parameters that could be used to benchmark data security on a network. Use the following website to help you with your research: https://www.techopedia.com/7/29801/security/how-can-security-be-measured
- Research the factors affecting bit error rate and why it should be used as a parameter for benchmarking a network design (you can specify the type of design, such as fibre optic or WLAN).
- the type of network traffic on the network
- the capacity of the current infrastructure
- utilisation of the network at various points in the network
- current traffic volumes for internal and external connectivity.
- The client budget.
- The current infrastructure.
- If the client specifies the vendor to be used.
- The quality of supplier products required.
- When the supplier products are needed.
- Check credentials and certificates.
- Review customer feedback and reviews.
- Can the equipment or software be customised?
- Are there additional or hidden fees or costs?
- Privacy and confidentiality of data.
- Does the products and equipment integrate with the current infrastructure?
- How easy is it to set up and train users?
- Is there future support?
- How are the updates or upgrades managed?
- Is there a SLA?
- the background and purpose for the report
- scope
- clients business specifications
- clients business requirements
- the selected solution
- network diagrams
- impacts of the design
- predicted forecast traffic demands and impacts
- benchmarks
- performance profile
- costs involved
- recommendations.
- the hardware, software, system architecture, processes, documentation that may be subject to change
- defining roles and responsibilities
- how these changes affect the users of the system
- addressing any skill gaps of users of the system
- providing a change management framework.
- coaching and mentoring
- support documentation, online support and quick reference guides
- online video training
- inhouse, online module training
- workshops
- one-on-one training
- group induction training
- certificate courses or formal external courses.
- specified in contracts
- requested through client requirements
- based on previous purchases
- computability requirements.
- maps, diagrams
- visual representations
- walk throughs
- data analysis
- spreadsheets
- project management documentation.
- explained clearly, logically and succinctly
- presented professionally and using effective communication skills
- free of jargon or technical speak that the client may not understand.
- client training feedback
- costings
- a design report
- an evaluation report and recommendations
- an implementation plan
- standards used such as international electrotechnical commission (IEC), institute of electrical and electronics engineers (IEEE) standards, internet engineering task force (IETF) standards or International Telecommunications Union (ITU) standards and Australian standards.
- a contract
- an email confirmation
- a formal agreement with confirmation of acceptance
- a telephone call followed by a formal contract.

