Advanced Computer Science Masters Project
- Subject Code :
7COM1039-0501-2021
- Country :
United Kingdom
- Background Research
Virtual infrastructures are entirely adequate to implement and design processes of security intelligence. Effectiveness of all types of infrastructures designing that are implemented with all available features and facilities of virtual modes are effectively working with completion of entire dealing process with structural data based on cyber security development process with intelligence systematically. Safety protection establishment process is functional to complete entire authentication process functionally to prepare appropriate authentication-based operations creatively . Troubleshooting based on several types of activities is adequate to conclude all prevention processes of cyber-attacks based on a cyber-system with help of virtualization infrastructure availability based on all applications of secure intelligence-based technologies constructively and productively. Detection and completion of evaluation process of systematic prediction processes are concluded with all available features and characteristics of relevant software application to analyse entire activities to execute alldetermination process related outcomes with high rated accuracy and efficiency structurally.
Cyber system processes are to be required proper effective features based on vulnerability and consecutive attack detection systems for completion of appropriate identification and investigation processes equivalently. In order to evaluate security intelligent technology implementation and application for preparing to visualize infrastructures, there are several types of accurate and essential cyber system-based rules, regulations and policies that are maintained and followed for avoiding any kind of occurrence of hassle and misconception in all over evaluation with collected datasets systematically . All kinds of operational activities based on development, designing and implementation process of virtualised infrastructures with security intelligence technologies are performed with all assistance of machine learning technology based on python code-based programming and relevant software platform, respectively. Moreover, this availability of virtualised infrastructures development with security intelligence process is most useful and effective to complete several types of recruitment of several organizations, government working sectors and all places to fulfil all necessary of public.
Figure 1: Virtualize infrastructure model designing
- Summary of progress
Evaluation process of establishment of virtualizing infrastructure to complete all prevention system implementation of cyber-attacks that are to be related to cyber systems is completely dependent on all availability of characteristics of secure intelligence technology. All of these establishment processes of infrastructure with security intelligence are to be concluded with all systematic designing processes of virtualization system based on code execution with python programming in Google Colab software sequentially (MuthuPandi and Somasundaram, 2020). In order for proper evaluation, there are different types of proper and suitable datasets to be collected and selected for completion of all initialization processes of infrastructure designing with securityintelligence technology. Proper datasets are to be considered from popular and trusted resources Kaggle to complete all required steep-based evaluations. After importing selected dataset in Google Colab software, Null values in dataset checking, removing all irrelevant availability columns in selected datasets, categorization of all characters in form of numeric and splitting an entire dataset into train and test for further implementation process of model designing are several essential steps for further progression process of project work.However, different types of graphical representation-based data visualization processes are to be developed with completion of execution of all codes for construction of heatmap, correlation and convolution matrices. On other hand, essential libraries are to be installed for completion of several types of models implementation such as decision tree, random forest classifier, naive Bayes, K-neighbours nearest algorithm, XCGBoost and support vector machine (SVM) for estimation of proper accuracy, F1 and efficiency scores with assistance of standardization scores for prediction process (Narayana and Jayashree, 2020). Completion of these constructive predictions is to be concluded after installation of proper libraries like NumPy, pandas, matlibplot and also sklearn for continuing all model implementation to continue entire progression work based on virtualization process with security intelligence technology. Moreover, summarization of all these several types of work activities is to be required to continue of total progression process based on project acquisition.
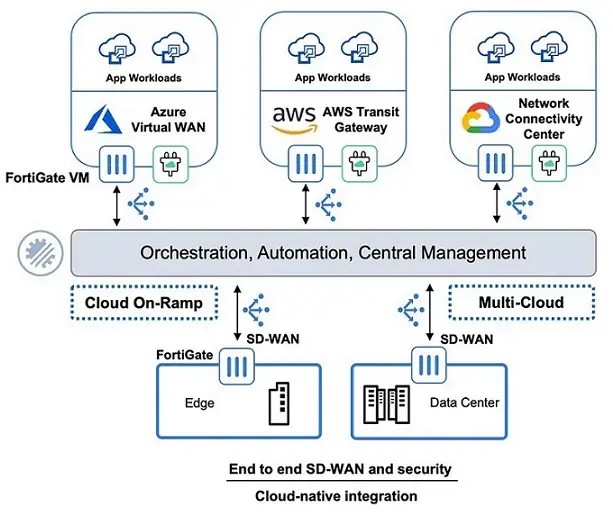
Figure 2: Designing of multi-cloud infrastructure with secure intelligence
- Ethical/legal/professional and social issues consideration
Several types of structural rules, policies, and regulations are to be required for completion of designing process of virtualization infrastructure with security intelligence technology to prevent any types of chances creation of cyber-attacks and hacking thatare to be related to cyber security implementation process with cyber systems. ICH processes related to different kinds of operations are to be maintained for completion of all data analysis based on security and confidentiality. However, there are several types of evaluation and execution-based data that are to be collected after completion of entire python code-based programming-based model design. Application and consecutive utilization process of secure lock-based systems are to be completely essential for completion of an entire data storage process with balancing and maintenance of authentication and confidentiality. Equivalent working structures implementation procedures are to be concluded with availability of several types of risk factors in a conventional therapeutic intervention (Ranaweera et al. 2020). Mistreatment for completion of all requirements based on project-based activities is to be considered as creation misconduct with presence of permitted protocol frequently. A crisis of insufficiently knowledgeable, concepts, and theories is required to complete consent- based activities, declaring several kinds of publicity-related topics with secure intelligence are responsive to creation of mental damage. Unacceptable process executions are to be related to maintenance of several evaluations with proper practices to preserve confidentiality and protection to keep all data safe, protective, and secure.
Moreover, Cyber security implementation processes are developed with security intelligence technology for creation of virtualization infrastructures with assistance of balancing and maintenance with several types of activeness of constructive rulesregulations, and pattern-based structural policies (Sharma et al. 2018). Data interchanging with execution procedures are to be concluded with completion of all following policies, rules and regulations that are most functional for development of infrastructure virtualization with security intelligence technology.
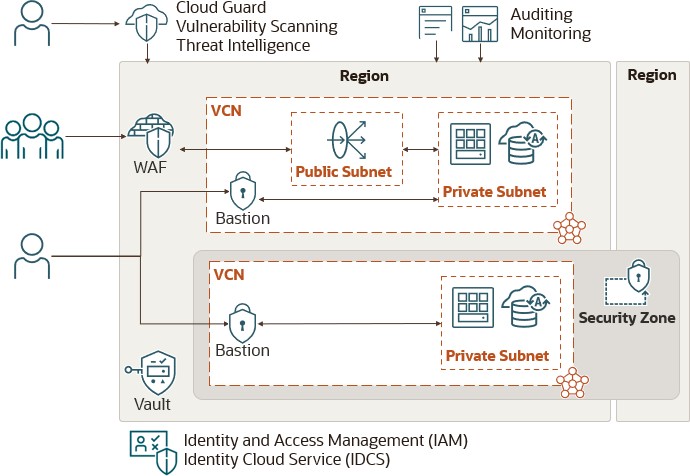 |
Figure 3: Secure intelligence utilization to implement security services
Project plan
The researcher will attempt to finish their procedures. Review literature, for instance, to learn about aspects of safety regulations, to recognise issues, to gather raw data, to review and modify data entered into a useful software programme, to enlarge the scope of educational processes through code, findings, outcomes, and discussions, and to create reports. Rules for informed consent disclosure, digital exchange, privacy, and data security are established under the data-driven cyber security and Accountability Act. Universal law is contained in the United Kingdom's Data Protection Act. It is also possible to design some telephonic surveys, which can be useful for managing some important factors.
The International Committee of Security Journal Editors (ICMJE) guidelines state that writers must make sure that non-essential identifying information (names, initials, and medical information) is not included in their works.
To carry out this research, a review of the relevant literature may be carried out to understand the idea of cyber safety. Different data controllers could use different Cybersecurity strategies. To expand the software-programmed model, the researcher may also use the Python software programme tool. The computerised utility can swiftly change records. A preliminary survey to gather data may also be finished.
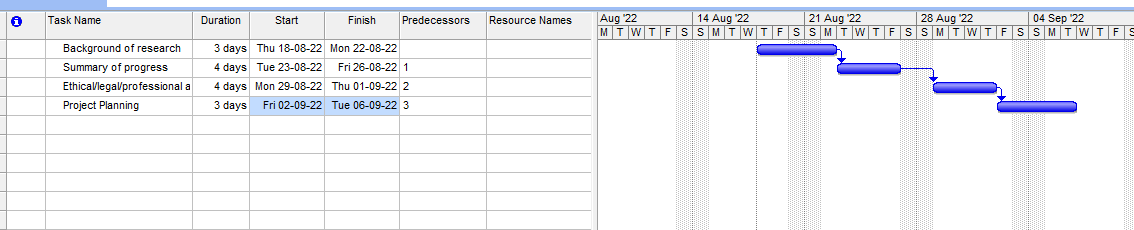 |
Figure 4: Gantt chart
(Source: Self-developed)
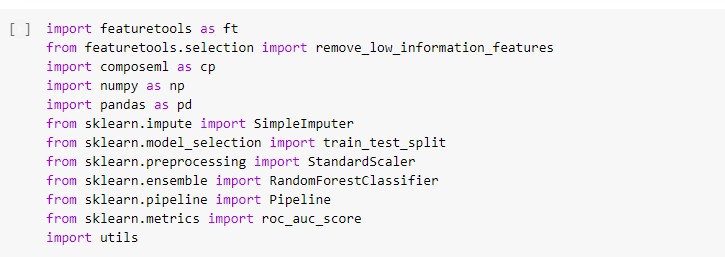
Application of feature selection
-
- Analysis on cyber security data
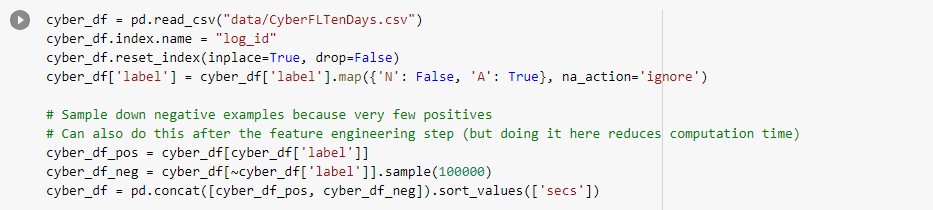 |

