BSBXCS402 PROMOTE WORKPLACE CYBER SECURITY AWARENESS AND BEST PRACTICES ASSIGNMENT
- Subject Code :
BSBXCS402
- University :
MILCOM Exam Question Bank is not sponsored or endorsed by this college or university.
- Country :
Australia
Topic 1: Cyber security awareness
Cyber security in the workplace
Protecting a companys information, data, assets, knowledge and systems, networks and business continuity, requires putting in effective measures to ensure that digital access is secure.
Cyber security practices can lower the risk of a cyber-attack such as unauthorised access, money extortion or data corruption.
Activity: Watch
The following video shows the anatomy of a cyber attack unfolding
https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html
(04:14)
Write down your key takeaways.
The trainer/assessor will facilitate a discussion about the outcomes from the video.

<>strong>How much do employees know?
An organisation can have the highest level of security in place, but it will not succeed if workers are not aware of the risks related to cyber security. Promoting workplace cyber security awareness and supporting effective practices can support the success of a business cyber security strategy.
Activity: Watch
Companies spend millions of dollars every year to protect their private data from cyber attack. However, ordinary people can undermine all their hard work with one mistake - and we often do. Most successful security breaches happen not because of sophisticated attacks, but due to human failures.
Watch this Ted talk by Mark Burnette: The humanity behind cyber security attacks
https://www.youtube.com/watch?v=pnADP41earI(18:22)
Write down your key takeaways.
The trainer/assessor will facilitate a discussion about the outcomes from the video.
Cyber security awareness means employees are educated and can:

As part of your job role in promoting cyber security the main question to always ask is:
ARE YOU DOING ENOUGH?
Developing awareness, supporting policies, procedures and best practices will be part of helping to ensure that you are doing your best to minimise the cyber threats to the organisation.
However, everyones job will be different with varying levels of authority and permissions to an organisations information and data systems. By identifying what employees know and understand about cyber risks and how these can be managed, will be an important step in the levels and consequences of risks that an organisation can face through cyber-attacks.
This must be relevant to roles and responsibilities as well as a holistic understanding of the organisation and industry within which employees work.
To find out what employees know and understand you will need to conduct surveys, interviews, consult and focus on their work activities within their job role so that the cyber security is contextualised and specific to the activities and duties that they are undertaking.
Once you have established what the level of awareness is, then the next step would be to have training and education to support effective cyber security practices.
For example, using a survey to find out information about how a person undertakes their job and the cyber security efforts that they currently use:
- How often do you change your password?
- Do you access the network from home? What security do you have in place on your computer?
- What should you do if you receive an email that includes an embedded link to a special deal?
- List three things that you do to protect company data in your job role.
Using an employees job description and focussing on questions that relate to their work role can provide a clear picture on an employees level of awareness. For example, someone who manages data entry:
- When using the database to enter in client contacts, how can you protect the data once entered?
- How are the client records kept private and confidential to other employees?
- What information can you give out about the client contacts in the database?
Using a program such as survey monkey or creating a list of questions that can be distributed by hand are two ways of collecting this type of information.
This information can then be used to identify what should be included in the cyber security awareness program. For example, the survey may find that 60% of staff are not changing their password often enough. You can then focus on the training and education to cover this aspect of cyber security awareness.
Activity: Research
Go to www.surveymonkey.com and check out how the surveys can be developed.
Read about survey design:
Survey Design 101
The trainer/assessor will facilitate a discussion about the outcomes from the research.
Developing a cyber security awareness program
Once you have found out what the level of awareness of cyber security in a workplace, the next step would be to develop a program that could be used to promote and manage best practices. The information collected from surveys, interviews, consultations, or other relevant research conducted can ascertain the level of understanding, if there are any gaps, what the risks are of these gaps and then what can be done to educate and train employees.
You may need to firstly identify:
- responsibilities and roles for cyber security in employee work areas
- a list of the associated risks and how to deal with them
- the causes and consequences if not managed.
The above factors can then be promoted through training and education and then outlined as compliance through organisational policies and procedures.
Common risks associated with workplace cyber security can be:

Although there will be different forms of cyber security threats for each work area, organisational best practices can ensure that common security risk measures can be enforced.
This could be best practices such as:
- The importance of password security
- Email, internet, and social media policies
- How to protect company data
- How to identify and report cyber security threats.
The different forms of cyber security threats could cover:
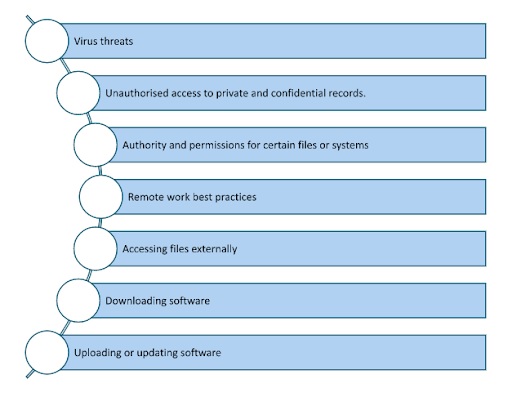
A cyber security awareness program can provide employees with the information, knowledge, tools and resources to manage threats. To work, you may need to make cyber security training mandatory for new employees and then update and repeat on a regular basis. Providing policies and procedures can also provide guidance and support compliance.
Cyber security policies and procedures
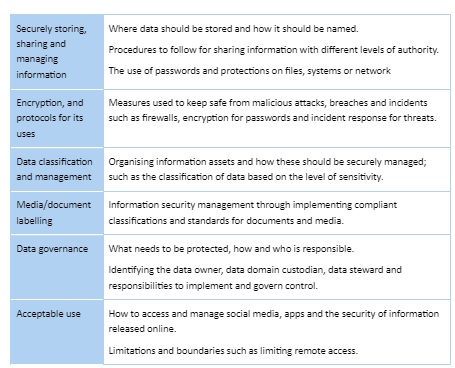
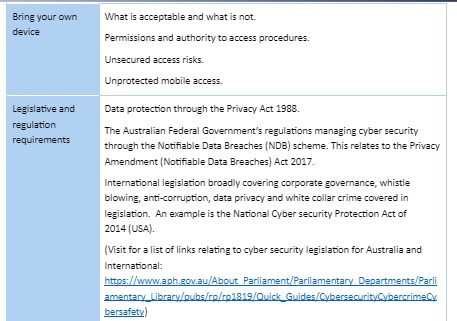
An organisations best practices and part of a cyber security awareness program can be implemented through policies and procedures.
They will be dependent on the industry and work activities being carried out as well as what has been identified as the threats to the organisation. Some broad areas could cover
: Activity: Read
Consolidate your learning by reading through the following information:
How to create a cyber security policy:
https://www.business.gov.au/risk-management/cyber-security/how-to-create-a-cyber-security-policy
The Privacy Act 1988 covering data protection:
https://www.oaic.gov.au/privacy/the-privacy-act/
13 Australian Privacy Principles governing standards, rights and obligations for protecting and securing data and information:
https://www.oaic.gov.au/privacy/australian-privacy-principles/
Notifiable Data Breach (NDB) Scheme and implications for unauthorised access of data:
https://www.mailguard.com.au/partner-blog/cybersecurity-legislation-ndb-20180202
International legislation information:
https://globalcompliancenews.com/cyber-security/cyber-security-around-the-world/
An example of a Cyber Security Policy:
https://ppl.app.uq.edu.au/content/cyber-security-policy
Take any notes to summarise what you have read and keep for future reference.
Communicating to personnel
An organisations cyber security policy and procedures should outline the assets that require protecting, what the threats are to those assets and the controls and guidelines for protecting them. It should guide employees on what can be shared, where and how, acceptable use procedures and the handling, storage and protection of sensitive information.
Therefore, the development of a cyber security policy must address key information relating to:

Communicating policies and procedures
Communicating the cyber security policies and procedures to relevant personnel and the way in which this has been done could greatly affect whether or not they are implemented and carried out successfully.
It can also go toward creating a positive cyber security culture and promote good practice to external stakeholders such as clients and auditors.
A structured approach to communicating cyber security policies and procedures could be as follows.
Firstly, you need to structure a communication plan to provide a framework and record of what is communicated, how, when, who by and what medium.
Next would be implementing a set of initiatives to inform employees of the cyber security program, such as online compulsory training modules or presenting policy frameworks to heads of department to inform teams.
Employees need to be engaged and follow through with the policy guidelines and procedures, so the communication may need to be gradual, consistent and regular.
Above all communication needs to be:
- clear
- concise
- relevant
- timely
- in a presentable format
- available on the most appropriate platforms and mediums.
Activity: Read
To find out more about effective communication, read the information at the following link:
https://www.proofhub.com/articles/effective-communication
Take any notes to summarise what you have read and keep for future reference.
Policies and procedures can be explained via training workshops, inductions, team meetings, workshops, as a compulsory aspect for new employees, or distributed via the organisations intranet, email or sent in paper format for signature to acknowledge their responsibility for compliance; an organisation needs to ensure that employees recognise and are compliant with security best practices.
The need to be able to support this through its effective communication of the policies and procedures can also be further implemented through reminders and restrictions, for example if an employee does not change their password within the time provided then they are restricted from accessing the internet.
It is therefore important that the implementation of policies and procedures are consistently monitored, reviewed and any non-compliance is recognised and acted upon.
Activity: Watch
Read the article and watch the informative video on high level cyber policy making
https://www.forbes.com/sites/cognitiveworld/2019/08/30/we-need-cyber-policy-now/#78789edb1e17 (43:12)
Take any notes and write down your key takeaways for discussion.
The trainer/assessor will facilitate a discussion.
Activity: Read
Read the following information on how to run effective cyber security awareness training:
. https://blog.ironbastion.com.au/running-effective-security-awareness-training/
Watch the embedded video.
Take any notes to summarise what you have read and keep for future reference.
Activity: Group work Cyber Security team project
Divide into small groups. Ensure you divide the work equally. This will be your project team. You are to work collaboratively as part of a cyber security team to help develop a cyber security awareness program for staff. This will include a policy, an information sheet and a training session.
The program will be eventually presented to your group in a training workshop situation (as part of the activity in the next topic).
Read the scenario:
Bam ford Community College has identified from a survey that the following will need to be included in a Cyber Security Policy:
- Best organisational practices for keeping student information private and confidential
- How to set, store and change passwords
- Email security measures
- BYOD (Bring your own device) procedures and rules
- Implications of Notifiable Data Breach legislation
- The 13 Australian Privacy Principles from the Privacy Act 1988.
The program must also include an information sheet:
- Organisational expectations including how to prepare, identify, prevent, detect, respond to security incidences
- Researched information on insights from cyber security trend analysis
(for example viawww.abs.gov.au or https://clutch.co/it-services/resources/how-employees-engage-company-cybersecurity-policies)
Ensure that the information is:
- Clear and concise
- Professionally presented
- Uses specific and industry-related terminology relating to cyber security
You will need to present the policy to staff and carry out a demonstration of at least one best cyber security practice using an appropriate technology platform to assist with promoting cyber security to teachers in their work role. Ensure you work collaboratively with your team to develop an innovative approach.
The policy must be written in a clearly structured and professionally presented document; the information sheet and training format and medium can be up to the teams.
Send an email attaching your policy and documents to your supervisor for approval and feedback (the trainer/assessor).
Your trainer/assessor will provide your group with feedback
Topic 2: Using effective cyber security practices
Reviewing cyber security practices
To support the effective implementation of cyber security practices, it will be necessary to review these to ensure that employees are following the policies and procedures communicated.
Consider the following cyber security practices and why you need to review these:
Virus protection Software may not be updated. Authorisation to protected files Staff may leave or change roles Acceptable use policy New social media apps being introduced or restricted Bring your own device New staff not following guidelines Legislative and regulation requirements These can constantly change so need to be reviewed and current practices updated accordingly. Review and updating cyber security practices should be a continual and cyclic process as threats can change as the business, industry, resources, staff and environment changes. Using reporting mechanisms for tracking changes and making updates can provide a formal process to ensure that any modifications are recorded and followed up.
Upon review you may find that the practices are:
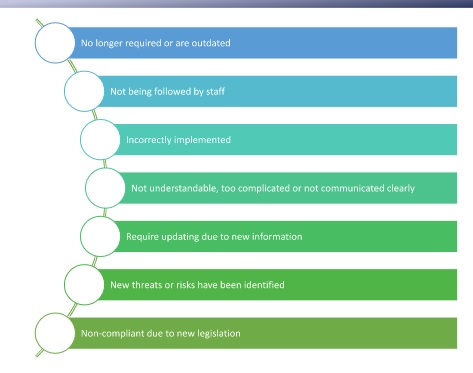
Activity: Watch
Read the article and watch the video on the top security predictions for 2021:
https://www.govtech.com/blogs/lohrmann-on-cybersecurity/the-top-21-security-predictions-for-2021.html
Write down your key takeaways.
The trainer/assessor will facilitate a discussion about the outcomes from the video.
Activity: Research and discuss
1.Review the following cyber security practices that are not being followed and identify what issues could arise from each.
A virus has been detected, contracted from downloading software not approved by the department
No updates have been performed on the operating system software.
Staff are not undertaking the mandatory professional development training on cyber security best practices.
2.Review the following Cyber Policy:
https://www.jcu.edu.au/policy/information-and-communications-technology/cybersecurity-policy
What principles could you apply to the above practices not being implemented?
The trainer/assessor will facilitate a discussion.
Training
Training in cyber security awareness can, as previously mentioned, promote a culture that supports effective cyber security practices.
There are many platforms, methods and training techniques that may be utilised by an organisation. For example: Conducting training workshops, developing online training modules, integrating into training and education professional development or informal instruction and promotion from senior management.
Some techniques for implementing and promoting workplace cyber security awareness include:
- simulation or role play activities such as phishing request emails
- using rewards and incentives
- promoting success
- distributing information on security issues and trends
- using videos, podcasts, webcasts or audio casts to promote understanding.
Facilitating training will need people with the knowledge, skills and experience to relay the information in an understandable and clear format that is appropriate to the work team. This can include consideration of the audience level, capability, roles and responsibility, work area, threats as well as communicating current organisational best practices that need to be promoted.
Maintaining updates
Once you have reviewed the cyber security practices, the next step would be to ensure that everyone is updated.
Security threats can emerge and also become less threatening or frequent, so you have to ensure that the policies and procedures reflect changes as soon as they occur and these are then communicated and any relevant documentation updated in a timely manner.
New information could include legislative changes, changes to staffing, identification of new risks or threats, changes in business processes, new standards, feedback from employees or breaches of security leading to new data security protocols being needed.
Updating could include:
- changing cyber security policies
- inclusion of new protocols or security encryption
- changing the impact of threat and the likelihood that it will happen
- further controls implemented to prevent ransom ware, phishing or hacking
- new best practices.
Updates could also include related records in risk registers, incident response plans and asset registers
.
- Arranging training and information updates could be by:
- Incorporating new training modules and conducting compulsory workshops;
- Distributing new information through updated policies and procedures;
- Announcing updates on the organisations intranet;
- Updating documents and records that relate to any updates received.
Any new information should be incorporated into policies and procedures, as no matter how small, it could have dire effects if not acted upon.
Topic 3: Reviewing cyber security
Cyber security is a constantly fast changing and evolving environment with new threats and trends impacting organisations.
Keeping abreast of what is happening, new advances or different approaches and strategies to cyber security best practices, will help to ensure that the organisation is up to date, current and aware of potential new risks.
The damage that could be caused to a business can be far reaching, often with devastating effects such as loss of reputation, data, staff and revenue.
So, what are the latest security threats and trends currently impacting organisations?
Activity: Watch Watch the following webinar on insights into todays cyber-attacks (2020)
https://www.brighttalk.com/webcast/7451/384866
The trainer/assessor will facilitate a discussion about the outcomes from the video
.Communicating improvements
To provide front line defence, ensure threats are kept to a minimum and cyber security awareness is continually updated, any review outcomes identified as improvements required, should be communicated in a timely manner.
Any new information that could help an organisation against cyber security threats, need to be integrated into policies and procedures and then communicated through training or modules to support the updates.
Imagine if you have conducted research and found that online chat messaging being used by your organisation can lead to phishing and malware attacks. You must act on this information and change the way in which the organisation uses the application, modifying the way in which they instruct staff in its use or providing a list of security risks associated with the app.
The most important factors here are:
- keeping up to date with changes, trends and new security threats
- reviewing outcomes and improvements
- communicating these in accordance with work roles and responsibilities
- conducting training and education to promote awareness and understanding
- updating policies and procedures and associated documents
- including organisational best cyber security practices across all work areas.

