55-408808 Introduction to Cyber Security, Maths and Cryptography
Section A Introduction
The 21st century has seen an unparalleled adoption of technology involving internetworked computers (the Internet). Computers are used in most aspects of our everyday life whether we are students, employees, employers, or private individuals. Security and privacy are very important as we not only have to protect our physical assets but also our data assets.
We are more reliant than ever on technology to control our home environments, music, memories, personal communications, and financial information. Remote working (especially now) is a must, requiring that we have secure communications with our schools, universities, and workplaces. Computer and network security work must address every level of a network or system (including physical, user-based, service-based, host-based, and network-based) to secure data, protect privacy and prevent criminal acts.
No single security component or method by itself can be expected to ensure complete protection for a network - or even an individual host computer. Instead, you need to assemble a group of methods that work in a coordinated fashion to provide protection against a variety of threats.
Section A Assignment Brief
You are asked to examine and re-engineer a small business/home office style network (Figure 1) to satisfy the key concepts underlying computer and network security: confidentiality, integrity, and availability.
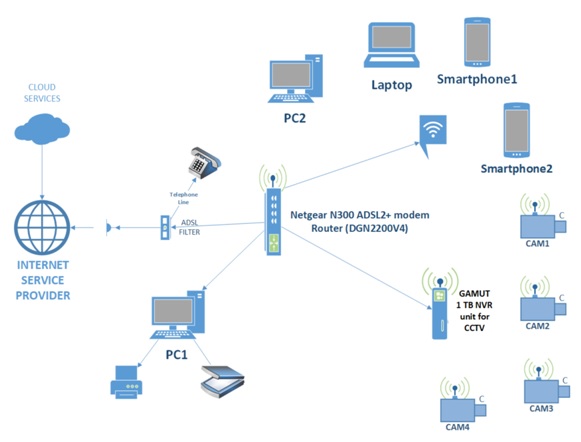
Section A Assignment Brief
You are asked to examine and re-engineer a small business/home office style network (Figure 1) to satisfy the key concepts underlying computer and network security: confidentiality, integrity, and availability.
Figure 1shows a small network comprising:
Two personal computers (PC1 and PC2), a laptop and a wireless router: Netgear N300 Wireless ADSL2+Modem Router DGN2200V4.
PC1 is directly wired to the Router using an RJ45 CAT6 ethernet cable, while PC2 and the laptop are connected by wireless/wifi to the router.
All the computers contain data (stored on the hard drives) as: lectures notes, labs, private and personal documents, family photos etc.
Two mobile phones (a Samsung J3 and an Apple iPhone 7) also connect to the internet using wireless technology
A scanner and a printer are connected to PC1 and are shared by all users on the network.
Using Figure 1 as a basis, you are asked to:
1. Identify/enumerate the various threats and risks in the devices and network. To do this you will consider the security/threat landscape (these are collective terms that refer to the devices and security involved, and the threats that they are commonly subjected to).
2. Recommend techniques to prevent or mitigate attacks on the devices within the network. Identify the technology/configuration you wish to use, the device/s that it is intended to protect, and explain why you feel that this choice oftechnology/configuration is beneficial to this application.
Device Specifications (for reference):
|
Device |
Description/Technical Specs |
|
PC1 |
Dell Optiplex 755 Intel Core2 Duo CPU E8400 @ 3.00GHz 2.99GHz Operating System: Windows 7 Enterprise, SP1 Malware Protection: Norton Security Premium Wireless 802.11 a/b/g PCI Adapter: Cisco Air-P12AG-E-K9 |
|
PC2 |
Intel(R) Core (TM) Duo CPU, E4500 @ 2.20GHz, 3 GB of RAM Hard Drive capacity: 250 GB Operating System: Windows 7- Home Premium, 32-bit Malware Protection: Norton Security Premium TP-Link TL-WN851N Wireless-N PCI adapter - uses 802.11n technology but is backwards compatible with the 802.11 b/g standard. |
|
Laptop |
ACER Aspire 5750 Intel(R) CoreTM is-2410, 2.3GHz with turbo boost up to 2.9GHz, 8GB DDR3 Memory Intel(R) HD Graphics 3000, up to 1760 MB Dynamic Video Memory Hard drive capacity: 750 GB ACER NplifyTM 802.1 b/g/n Wireless adapter Operating System: Windows 10 Professional 64-bit OS, SP1 Malware Protection: Norton Security Premium |
|
Netgear N300 ADSL2 DGN2200V4 Router |
IEEE 802.11 b/g/n 2.4GHz Four (4) 10/100 Fast Ethernet Ports One (1) ADSL2+ Port One (1) USB 2.0 Port Built-in ADSL2+ Modem IPv6 Support (Internet Protocol Version 6) Live Parental Controls Security Wi-Fi Protected Access (WPA/WPA2PSK) Intrusion detection and prevention (IDS) Denial-of-service (DoS) attack prevention . and many more - see manual for details |
|
Wireless CCTV (Gamut 2MP HD-TVI) |
Some specifications can be found at Gamut 2MP HD-TVI 4 Bullet Camera CCTV System SpyCameraCCTV . To make additional security recommendations, you will need to conduct additional research into common security risks of IP CCTV systems and the means to mitigate these risks. |
|
Phone Handset 1 |
Samsung Galaxy J3 |
|
Phone Handset 2 |
Apple iPhone 7 |
Section B Introduction
Cryptology underpins many protocols in cyber security and, by having an awareness of the fundamental classical and modern techniques in Cryptography and Cryptanalysis, we allow ourselves a broader understanding of how weaknesses can be avoided. The mathematics inherent in these cryptological techniques further enables us to be systematic, clear, and precise about our understanding and presentation of data, numbers, and figures.
Part 1: Classical Ciphers
Question 1.Decrypt the following ciphertext using a Caesar cipher. You may use Excel to help you.
TDSLWWTYOFPETXPMPLAZPE
(10 marks including 1 mark for identifying the quotation.)
Question 2.The following ciphertext has been obtained using a General Substitution cipher. Use an Excel spreadsheet to decrypt it. Explain all the steps of your working.
RSIUBZAWX JAWA MAFAHSUAM LC XARWAZ EDRP LC JSWHM JDW ZJS IDLCHN ZS EWADP RSMAX SWMLCDWN UASUHA MLM CSZ GDFA DRRAXX ZS RSIUBZAWX EARDBXA ZGAN JAWA TAJ LC CBIEAW DCM ZSS AKUACXLFA XSIA UASUHA USXZBHDZAM ZGDZ ZGAWA JSBHM CAFAW EA D CAAM TSW ISWA ZGDC GDHT D MSQAC RSIUBZAWX LC ZGA RSBCZWN DCM DXXBIAM ZGDZ SWMLCDWN UASUHA JSBHM CAFAW GDFA D CAAM TSW RSIUBZAWX XSIA ST ZGA OSFAWCIACZX DZZLZBMA ZSJDWM RWNUZSOWDUGN ZSMDN JAWA TSWIAM LC ZGDZ UAWLSM DCM ILWWSWX ZGA SHM DZZLZBMAX ZSJDWM RSIUBZAWX JGN JSBHM SWMLCDWN UASUHA CAAM ZS GDFA DRRAXX ZS OSSM RWNUZSOWDUGN LC DMMLZLSC ZS ZGA HLILZAM DFDLHDELHLZN ST RSIUBZAWX DCSZGAW UWSEHAI JLZG RWNUZSOWDUGN LC ZGSXA MDNX JDX ZGDZ RWNUZSOWDUGLR PANX GDM ZS EA MLXZWLEBZAM SFAW XARBWA RGDCCAHX XS ZGDZ ESZG UDWZLAX RSBHM XACM ACRWNUZAM ZWDTTLR SFAW LCXARBWA RGDCCAHX OSFAWCIACZX XSHFAM ZGDZ UWSEHAI EN MLXUDZRGLCO PAN RSBWLAWX JLZG XDZRGAHX GDCMRBTTAM ZS ZGALW JWLXZX OSFAWCIACZX RSBHM DTTSWM ZS XACM OBNX HLPA ZGAXA ZS ZGALW AIEDXXLAX SFAWXADX EBZ ZGA OWADZ IDXXAX ST SWMLCDWN UASUHA JSBHM CAFAW GDFA DRRAXX ZS UWDRZLRDH RWNUZSOWDUGN LT PANX GDM ZS EA MLXZWLEBZAM ZGLX JDN CS IDZZAW GSJ RGADU DCM USJAWTBH UAWXSCDH RSIUBZAWX ILOGZ XSIAMDN EARSIA NSB YBXZ RDCZ XACM ZGA PANX AHARZWSCLRDHHN JLZGSBZ ZGA WLXP ST LCZAWRAUZLSC
Question 3.
a) Use the Vigenre cipher with keyword ALPHABET to encrypt your surname and first names (12 letters in all), e.g., `John Smith becomes plaintext `smithjohnsmi
b) The following ciphertext has been obtained using a Vigenre cipher. You are provided with a table of interval values and possible key sizes. Determine an appropriate key size and use an Excel spreadsheet to decrypt the ciphertext. Explain all of your steps and provide evidence such as suitable Excel screenshots.
|
sequence |
interval |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
|
AAPX |
162 |
X |
X |
X |
X |
|||||||||||
|
MJZQ |
143 |
X |
X |
|||||||||||||
|
KMOJ |
135 |
X |
X |
X |
X |
|||||||||||
|
WDLW |
36 |
X |
X |
X |
X |
X |
X |
|||||||||
|
BMZQ |
252 |
X |
X |
X |
X |
X |
X |
X |
X |
|||||||
|
YOIG |
171 |
X |
X |
SLAMFVHERZHGHSBLPENPVDTNECHRVTNYQSYLJJZRUBSRUWWPRYPIOHRLTHUUIYWKMKAJITOLCPBTQPECGSHZXMIWQUALLBYNVZPPOMWJAMRQHPUBYIXTRJZWYRMGSDJPKTQKSXSQAQGLIROENVCZMBXSHYVAMTNLTJDNZTIMGCBLAWZWITSLYKMONKIDGKDVMTELPUAAPXDKEYEABAXIQRDXYOKHRUICFEHTTUXPTFWAQHSAEDUATWMJKEDKZPAIJVWPUOHVWHWQAXPLZMJZQTQWSABSBYCQOBKAFXTWLYHBBTVWNUAHBXFVIPGBVZGJEXJSAZWYHZCAWKNZTUPMNVUZBXRAASLYOUBSQQTCAAPXSMGPVOPBRTNWPFQYMDJGHTVPYQUZBMZQYOIGSMPDDJKANUXPJWDLMJZQZLOAUBHKIACLPAMGXQKYDPBZXFBXSHOHUXYQQPWDLWKJBMNDHKMOJTSAPAUBLNVMYIKYUTYQSYWDLWKDIROFKTXNYMVDFELVVJALZZLYWFNAIZILYWONLMYJLYWOFJPJVAJCKJKVJSPVARXBIXVYOIGLQRRWDPATSKMPQPHZMNVXZDOJQXSKIEKAKMOJTSAPAUBHKKSXSQAMKHWREUKSTXIKSXPQUQVFBMZQOUMMBWVVVLYWFNAIDHBMWKYTIDVWULBSMBAHJZQOJKSYWWJBUJBAPHJWMHUTIZUYVUIZBICVKUWIUWWTWAZQWJASQWDLEHWTHCHLSIVNVKXROAUTNTEYGIHVRJFGFUOPWGXEMEKPLTXHWQXXJPKTYQSYVBVZFFVCLSLSQVFBMZQOAPXXMGZQPHKMXUYDWXLUTIMWPFQYMTLIMYVPIWMMMEGHOKZHUXMYJWULMMMMYMAJBBTVSQLHSMZNBMXDPLUXXAERHOHBIWMWPQPOWPJDICWDLAHQCXTRJVNLJKYCLPFXKTJPPPOSIZXEIWOXLPBSLSEKAYIKJIWZIYVUFZVMNDPPWGXBINKJVTHLGGZQPLUITZECBYYGIYWKCDLOGBXCRLEHLBHRMIEWDLZXVCMCHILVMXQREKWAQMXCWPZKBTWNUTZVAZCVMAIGHNLQGHWRGHJPMGHMWZQPOMLDAXPPQZMKXIWERASQFNVEEHIHVRTNXSHXLVXKQXDRBAMEJXVZFAZABSOXSHXLAMPVSHQYYGIYWKCDLOQVUZSMOATQLYPEERBWZBAIGJSNLDXSBMYJPOMNSIYEKKYQSJLIIWNHKMNWRZIEUNHWUEELKUNKTUGZPIBVBHIXTRJZWOJZEYLJZMVZZINKWUVXQQRZUZLZMTCWPFNFXMTOVLSDFBHNVWFUAWZBAIGJKKDMOJZMELOJCKWMREOUUMVJAWLUUMWKYPINRITCGNKEELJNXTWBMPVPVAAFZILNAFEANKLTVGUWPSBSYRKUMXQAIEKEZQLIWRPEUZMGIQRRWDLSXDQRLGRHVVJWZPUOVUXXMGFUAJPTSVIWVQJPTXXVTYWAMVTCVTHNVZKJOMDWAYMWRIMWDLYQOFBINRJCMKXIXTRJIMMBMIYWSVXXTXPPZEAPGTXVTRNHKJZIMYWWUKXNAENRITWGTKGFUNLVVJQRMXOPVXXALZZACMKFVHTWEZCGWMEWLOAQVYWIISAJBBSQXTDHICLNVIDVYVVMFKXDWKIMITAXARJLLETVKPQKBOAKWVVHUZBHGMXCDJZUBYBIOEUZWFJXLJVEJIERMEYVPOMVTAXLQZKMEFGMXSKZMWGGXSLORMRIQWEUEICMNWRAUKITXRQWLPWQWKGIVCLAYBHYPIEUWUAYJZSQEQZQGJAWNRITCGNKEELKUAMTTECJAAMEJXVZFAZABSORPWSVZDX
Part 2: Modern Ciphers
Question 4. Upper case ASCII letters A-Z are represented by the denary numbers 65-90; lower case ASCII letters a to z are represented by the denary numbers 97-122. The decimal value is converted to an 8-bit binary string and to encrypt any letter its 8-bit binary representation is combined with an 8-bit secret key using bitwise XOR.
A 3-letter word has been encrypted one letter at a time. The encrypted word is fgq. If the secret key is 00100010, then what was the original plaintext message.
(15 marks)
Question 5.Using an Excel spreadsheet encrypt 16 letters (using ASCII) from your surname and first name (e.g., Alex Corner would be CornerAlexCorne) to produce a ciphertext in hexadecimal, by applying the first round of AES (Rijndael) as far as the Shift Row stage. Use the following key :
|
7E |
1B |
60 |
8B |
|
2A |
EC |
F1 |
37 |
|
59 |
5F |
BC |
19 |
|
D4 |
0A |
EE |
CF |
Explain all of your steps with supporting evidence (e.g., appropriate Excel screenshots) and provide the encrypted value at the end of each stage. I.e., after Add Key, after Byte Sub, and finally after Shift Row. Do not attempt the Mix Columns stage.
(35 marks)
Question 6.Use the RSA cipher to decrypt the word TfG. The public key is , . Decrypt a single letter at a time. You may use an Excel spreadsheet but for full marks you must explain each step of your calculation.
(30 marks)
Question 7.Alices RSA public key [; ] is stored in binary as
[1111010011000111; 00001011].
Eve wants to find Alices private key by factorising .
- What are the prime factors of and what is Alices private key?
- What is the maximum number of ASCII letters that can be encrypted in one go and sent to Alice (assuming the message has no padding)? Explain your answer.
- Alice decides to change the value in her public key. Which of the following choices are not allowed? 3, 17, 19, 23, 31, 35, 45, 65. Explain your answer.
(20 marks)
Are you struggling to keep up with the demands of your academic journey? Don't worry, we've got your back!
Exam Question Bank is your trusted partner in achieving academic excellence for all kind of technical and non-technical subjects. Our comprehensive range of academic services is designed to cater to students at every level. Whether you're a high school student, a college undergraduate, or pursuing advanced studies, we have the expertise and resources to support you.
To connect with expert and ask your query click here Exam Question Bank

