Bridging the gap between you and the technology: Understanding the Application Layer
- Country :
Australia
Activity 1: Understanding the Application Layer using HTTP
We use different internet applications to do many things in our day-to-day life including accessing web, e-mail, and even sharing files. It seems these applications are straight forward as we can simply use these applications without knowing how they work. The application layer in the TCP/IP model is the interface that prepares our communication for transmitting over the computer networks. Lets do the following activity to learn more about the application layer protocol.
This activity is a group activity. Therefore, you need to form a group of four (4) people. At your table (or in MS team breakout room), discuss the following questions and activities with your group members. Remember to take notes as they will help you prepare your OnTrack task submissions.
- Why do we need application layer protocols?
- Discuss some examples of application layer protocols.
- Lets consider one of the popular application layer protocols, HTTP to learn the principal operation of HTTP. To carry on this discussion, we can do a small role play.
- Once you have done the above steps (a to d), now assume a Web cache which is also called a proxy server introduced to the network as shown in the following diagram.
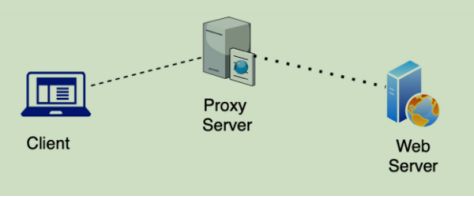
- Lets do another role paying to understand the role of proxy server/ web cache. For this scenario, one group member who acted as a client can now act as a proxy server. You can assume that the proxy server has the objects that Client 1 requested but does not have the objects requested by the Client 3.
- Now repeat Steps c and d for the scenario described in Step e.
Activity 2: Analysing HTTP in Wireshark
Having a basic understanding about the Wireshark packet sniffer through Active Class 1, we are now ready to use Wireshark to further investigate HTTP. Today, we will explore some important aspects of the HTTP protocol including the basic GET/response interaction, and HTTP message formats.
You can follow the following steps to conduct the analysis.
- Open your web browser and clear the browsers cache if you have not done that already.
- Open the Wireshark packet sniffer and start the packet capture (Wireshark captures the packets by default when you open it for the first time)
- Enter the URL with http (not https) into your browser. If you are unsure what to use, you can use http://www.columbia.edu/~fdc/sample.html .
- Stop Wireshark packet capture once the page is loaded in your browser.
- We want to analyse HTTP. Therefore, you want to filter out http responses. To do that, enter http in the filter.
- Now you can analyse HTTP, requests, responses, and sequences.
- By analysing the HTTP responses, you should be able to answer the following questions,
- What is the sequence of HTTP message exchange?
- Are we using persistence/ non-persistence connection?
- What are details you can find in HTTP GET message?
- Check the packet details in the middle Wireshark packet details pane. Can you identify the details in Ethernet II / Internet Protocol Version 4 /Transmission Control Protocol / Hypertext Transfer Protocol frames?
- What is the HTTP version your browser used?
- Identify the response message received from the server?
- What is version of HTTP that the server is running?
- Can you identify the IP address of your computer?
- Can you identify the IP address of http://www.columbia.edu/ server?
- What is the status code returned from the server to your browser?
- When was the HTML file that you are accessing last modified at the server?
- Repeat the analysis by accessing a different web page of your choice.
- What happens when you use https? Can you analyse the responses? Discussyour answer with your group members.
Note:
You need to provide a summary of your learning and evidence that you have achieved each of the learning objectives listed at the top of this activity. You can use the discussions/ screenshots that you have had while completing the activity as part of this evidence.
Above and Beyond Tasks:
Those who are targeting for Credit and above can complete the following tasks as part of Task 4.1C and 5.2D to demonstrate your deeper understanding on application layer protocols.
- Analysing TLS
- Open your web browser and clear the browsers cache. Open the Wireshark packet sniffer and start the packet capture
- Enter a URL with HTTPS in your browser.
- Stop packet capture and you can start analysing the packets. Explain the operation and handshake process of TLS using the screen captures of Wireshark.
- You need to clearly identify the message sequence and protocols used (including transport layer protocols) before your browser sends the first HTTP GET message to the relevant web server.
- Can you analyse HTTPS in Wireshark? Explain your answer. If yes, provide evidence on how we can do that. If not, is there any alternative method we could use to analyse HTTPS?

