CSE1ICB Malicious Software - Network Simulation Assignment
- Subject Code :
CSE1ICB
- University :
La Trobe University Exam Question Bank is not sponsored or endorsed by this college or university.
- Country :
Australia
Instruction
- Please submit via CSE1ICB LMS page Assignment submission section.
- This assignment is due on Sunday 9th April 2022 before 11.59 pm.
- Evaluation: 20 marks (= 20% of your final grade)
- You must submit your assignment only as a PDF file for Part 1 and Packet Tracer file (.pkt) for Part 2.
- Please write your full name and student number on the top of the first page.
Part 1: Malicious Software (15 Marks)
Malicious software (malware) has been a fixture of the cybersecurity landscape for decades. The target, technology, and impact of malware has changed over the years, but it remains a common tactic used by cybercriminals to cause harm to both individuals and businesses.
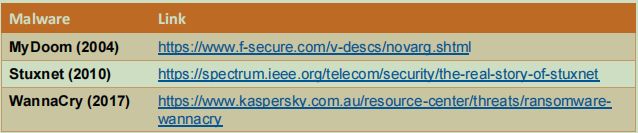
Security researchers across the world dissect and analyse each large malware outbreak, and a lot of their findings are publicly accessible on the Web. Several (in)famous malware samples are listed in the table below, along with a sample article describing their outbreak.
Select one of the samples provided (or choose one of your own from your research) and answer the following questions relating to the malware and its outbreak in the wild.
- What type of malware is it (worm, trojan, etc.)? Briefly describe what distinguishes this malware type from others.
- What was the intent behind this malware, and who were its targets?
- Briefly describe what vulnerabilities this malware exploited to infect its target systems.
- What negative impact did this malware have on its victims and/or their systems?
You should use between 500 and 1000 words in total to answer these questions. You should research other sources of information from reputable online resources such as malware research groups, security vendors, security journalists and academic papers if possible.
Part 2: Network Simulation Broadcast domains (5 Marks)
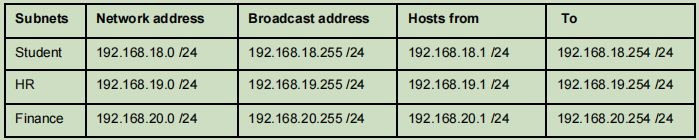
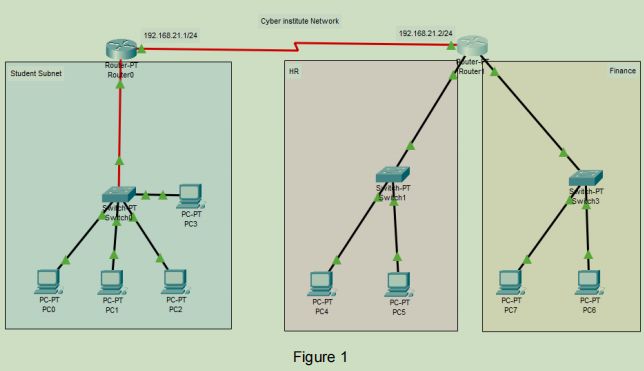
Cyber institute has given the IP address of 192.168.0.0 /24 The university creates three subnets as HR, Finance, and Students. Students subnet is connected to the router 0 as in Figure 1, and HR and Finance subnets are connected to router 1 to separate Students subnet broadcast domain for security reasons.
Create Cyber institutes network in Packet Tracer. Ensure that all the hostnames and network addresses are well labeled. Refer to the following table to configure the network and select appropriate addresses (IPs) to all hosts, routers interfaces, default gateways. Make sure subnet masks are correctly defined as required.
All PCs in all subnets should be able to ping each other. Please note that you need to configure routing table in both router (refer to lab 4 if needed).