IT Infrastructure Management and Virtualization Techniques ITC4052
- Subject Code :
ITC4052
Task 1
Hardware Inventory
Hardware inventory is a basic form of IT asset management that helps organizations properly manage their hardware assets (Tan, 2003). Inventory lists all hardware and its characteristics such as the specification, the number of items available, and where they can be obtained (Karri et al., 2022). The detailed inventory for this assignment includes:
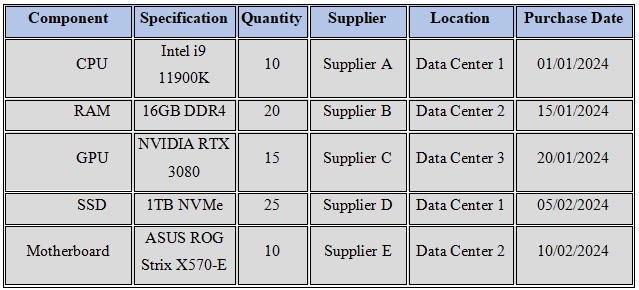
One of the practices that are important to good IT management is the production of an inventory of hardware used in the company. It entails the creation of a detailed list of all physical assets applied in a companys IT system. Key categories of hardware include:
1. Client Devices:
- Desktops and Workstations: Required for tasks that may be time-consuming to complete in ordinary hardware.
- Laptops and Mobile Devices: Allow choice and work from home.
- Thin Clients: Use of central server for computation advised for simple computational tasks.
2. Servers:
- File Servers: Perform a large part of the file storing and retrieval of files.
- Database Servers: Process and deliver instantiation of database.
- Email Servers: Greet on phone, handle e-mail communication.
- Application Servers: Housing and operating application service.
- Web Servers: Aggressively host websites and web applications using agile development and cloud architectures.
- Backup Servers: Backups should be a given with any data.
3. Network Equipment:
- Routers: Transmit data messages between networks.
- Switches: Establish hookups and linkages within organizations.
- Firewalls: Play the role of a firewall or a filter of the traffic passing through the network.
4.Storage Systems:
- Network-Attached Storage (NAS): Device designed for Real-Time collaboration and that resides on a network-accessible server.
- Storage Area Network (SAN): Server storage high-performance fabric connection.
- Direct-Attached Storage (DAS): These storage gadgets are fixed locally on a particular server hence known as local storage.
5. Data Centre Equipment:
- Cooling Systems: Control temperature to ensure improved performance of servers.
- Power Supply Units: Provide proper power to all the hardware parts.
- Rack Mounts and Cabinets: Outfit and further the durability of tools.
Risk Strategy
Risk matters that must be managed focus on elevation, evaluation, and particularly minimization of possible dangers to hardware. Key risks include:
- Hardware Failure: The physical components may break down because of wearing out or due to some physical influences from the environment. To lessen this risk there must be frequent checkups and or services to the equipment. Redundancy can also help to avoid data loss, for example by organizing storage in RAID.
- Performance Issues: The decision for a degraded performance can stem from insufficient hardware. There is always an assistant refresh of components and resource management which assists in maintaining effectively the delivery of performance (Lee, Gaffar, Mencer & Luk, 2005).
- Data Loss: Due to the failure of hardware or poor backup mechanisms employed the loss can happen. The general principle of the procedure is to update, and the periodicity of the backup activities check will ensure the data recovery means.
- Monitoring Tool Proposal: The hardware should effectively be monitored through a general monitoring tool to help monitor the health and performance of the hardware. Key features should include:
- Real-time Monitoring: It keeps track of CPU usage, memory usage, and the disk health of a machine.
- Alerts and Notifications: Can give instant notifications concerning certain problems, for instance, hardware failure.
- Reporting and Analytics: Creates reports of performance trends and likely risks in the current environment.
- Integration Capabilities: Complements traditional IT management software.
- Scalability: Does not restrict the kind of hardware components that it can used or the environment that it can be used in.
- Optimization Plan
To optimize hardware resources:
- Resource Allocation: As needed based on the workload they should be upgraded, to meet the workload demands of the software.
- Virtualization: Simplify and optimise workloads using virtual machines.
- Performance Tuning: Optimize parameters and other characteristics.
- Capacity Planning: Supervise the use of the hardware and estimate future requirements depending on the increase rates.
Predicting risk and developing an organized hardware inventory is crucial to an enterprises IT company. Through such approaches as categorization of hardware, risk identification, and other measures, an organization can have efficient operations, and security measures as well as improve its capacity to be more of a carrier of risks. Other than the policies, tracking software and optimisation strategies also supplement the efficient management of hardware and great IT support for the organization.
Task 2
Here and in this paper, the process of setting up a Virtual Machine utilising VirtualBox is explained as well as the assessment of the VMs performance. This includes how the virtual machine configuration procedure is done, how the VM efficiency and its capacity can be rated, and recommended measures that can be taken to improve it.
2. VM Creation Process
Setting Up VirtualBox
VirtualBox 7.0 was installed from the VirtualBox official website. This tool was used to create and manage the VM environment.
Creating the Virtual Machine
1. Launching VirtualBox:
Open VirtualBox from the application menu.
2. Configuring the VM:
- Name: Entered "Windows10-VM".
- Type: Selected "Microsoft Windows".
- Version: Chose "Windows 10 (64-bit)" based on the ISO file.
- Base Memory:
- Allocated 2048 MB (2 GB) of RAM.
- Hard Disk:
- Created a new virtual hard disk with the following settings:
- Size: 20 GB, dynamically allocated.
- Type: VDI (VirtualBox Disk Image).
3.Attaching the Windows 10 ISO:
- Storage Configuration:
- Selected the "Storage" tab.
- Under "Controller: SATA," clicked on "Empty."
- Clicked the disk icon next to "Optical Drive" and chose "Choose a disk file..."
- Browsed to the location of the Windows 10 ISO file, selected it, and clicked "Open."
4.Starting the VM:
- Clicked "Start" to boot the VM.
- Followed the Windows 10 installation prompts to complete the setup.
Installing VirtualBox Guest Additions
1.Inserting Guest Additions:
- With the VM running, select "Devices" from the VirtualBox menu.
- Clicked "Insert Guest Additions CD image..."
- Followed the installation prompts inside the VM to complete the installation.
3. Performance Analysis
Monitoring System Resources
1.CPU Usage:
- It was carefully observed through the help of Task Manager. It was characterized when using the computer to install other programs and when executing other tasks simultaneously.
2. Memory Usage:
- MONITOR WITH TASK MANAGER. Most tasks were easily handled with the 2GB RAM assigned for it though during heavy multitasking, the memory utilization got close to the upper limit.
3. Disk Activity:
- Controlled and monitored by using the Windows Task Manager. Measuring its usual read/write performance and reported every lag time.
Benchmark Testing
1. Benchmark Tools:
- Pass Mark Performance Test was used to measure the CPU and the memory performances (Spradling, 2007).
- Results:
CPU Performance: The CPU performance was average being able to meet the needs of a usual, everyday user or casual use of programs and software. Using the benchmark scores it was evident that the CPU adhered to the performance expectations out of the resources provided.
Memory Usage: The memory performance was satisfactory but stressed continuously that the laptop has 2 GB RAM and it seemed to be working to the utmost limit during operation. This pointed towards the fact that the presence of more RAM means better performance of the entire system.
Identifying Bottlenecks
1. Observations:
- CPU: It takes high CPU rates using many resources by the application at some instances.
- Memory: The usage of memory was often at its sold limit, especially during multitasking and operation of more memory-intensive applications.
Summary Table
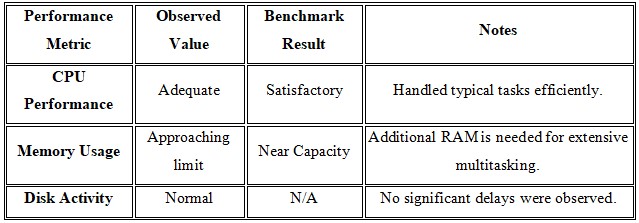
Enhancement Strategies
Optimizing VM Settings
1.Memory Allocation:
- Suspending the currently running application and providing more amount of memory up to 4096 MB (4 GB) for the smooth operation of multiple applications or for applications that occupy more memory zones.
2.CPU Cores:
- Assigned extra virtual CPUs (as 2 vCPUs) to provide more power for the computing tasks.
Software Updates
1. System Updates:
- Checked that Windows 10 and all drivers that are needed for the proper functioning of video cards were of the latest versions to reduce the chance of crashes and improve performance.
Storage Improvements
1.Expanding Disk Size:
Some enhancements such as increased virtual hard disk size from 10 to 40 GB to allow for installation of extra software and storage of data.
2.SSD Considerations:
Thought about using the SSD to drop the virtual disk on to increase the read/write operations per second. The VM was able to be initialized and installed on the platform of Virtual Box with high efficiency. The performance testing showed that the level of CPU was acceptable most of the time, but the amount of memory was a real problem in multi-tasking. The allocated memory can be improved, the number of allocated CPU cores can be enhanced, and adjustments to the storage help optimise the overall performance and enhance the efficiency of the VM.
Task 3
According to the industry best practices, ethics, and social responsibilities are important aspects that IT professionals must meet when handling hardware maintenance. First, these principles mean that the maintenance of the hardware is in harmony with the technical, social, legal, and ethical demands present in society.
Industry Best Practices in Hardware Maintenance
Procedures that are majorly used in industrial facilities include the recognized norms for hardware maintenance that are meant to enhance the durability, reliability, and efficiency of systems that are made of hardware components. Some of these are incessant updates, scheduled maintenance, proper paperwork, and adhering to the required safety measures. One of the key areas is that the firm uses the IT infrastructure library (ITIL) approach which is set to ensure consistent improvement and service (Zhu, Mauro, & Pramanick, 2003). ITIL teaches the implementation of effective practices for the proper maintenance of computer systems, which will reduce the possibility of frequent breakdowns and improve the performance of the hardware as well.
Ethical Considerations in Hardware Maintenance
IT ethical practices are well-defined sets of principles that seek to enhance the rights of individuals, the interest of the clients, and the welfare of the public. For example, the New Zealand Institute of ITP Code of Ethics covers principles and guidelines like; respecting individuals, safeguarding clients interests, honor, integrity, and diligence. In HW maintenance, this implies that so many actions are not to harm users or put data security and/or privacy at risk (Nygrd & Katsikas, 2024).
For instance, any time replacing or fixing elements, it becomes moral to erase all the individual information to save the prior proprietors prevue. Similarly, to software licenses, IT professionals need to conform to the rules set out in the End User License Agreement (EULA) whereby software cannot be used improperly, and any illicit copy is simply prohibited.
Social Responsibility in Hardware Maintenance
Thus, social responsibility in IT goes beyond legal obligations and duties; it means bringing benefits to society and reducing negative impacts on the environment. In hardware maintenance, it can be accomplished by taking environmentally friendly measures like repairing rather than replacing old hardware, using energy-effective devices, and avoiding the generation of electronic waste. Transportation from the linear model of the extractive-consumer-dispose model to the circular model of the design-use-recycle model must be undertaken to minimize the ecological impact of IT operations (van Liemt, 2007).
Task 4
Collaborative Analysis of Hardware Problems
Hardware issues should be analyzed collectively during IT project management since several people or departments may be involved in a quest to identify the problems and find solutions to them.
Importance of Collaboration in Hardware Problem Analysis
In terms of information technology projects, hardware issues may occur at different levels: during implementation, in the middle of a project, or during sustenance. Such problems may contain one or many of these: the performance of the code, compatibility issues, or even physical failure of some hardware (Edfelt, 2023).
Key Techniques for Effective Collaboration
1. Structured Communication: Different information that must be exchanged should be conveyed in a clear and definite manner due to the nature of collaboration. Ensure there is a proper flow of communication through daily progress reports, proper documentation on emerging challenges, and effective feedback channels that keep everyone in the team informed.
2. Role Clarity: In the process of conflict solution, it is important to determine what roles and duties each of the team members has. Every member of the team must know what his part is regarding the analysis step. For instance, while the system administrator may diagnose a given equipment for general faults, the network engineer will look at it from a network perspective.
3. Utilization of Best Practices: Effective change management and professionalism properly prepare the organisation and the assessment of the hardware problem is done systematically. These include following standard procedures in conducting a test, reporting results as well as applying changes.
4. Incorporating Feedback Loops: They help in introducing future stages of refining the process of problem-solving into feedback loops. Then when a solution has been proposed, one is supposed to seek an opinion from all the people involved to determine whether the proposed solution was satisfactory and if there were any other emerging problems (Nuyens, 2009).
Challenges and Solutions in Collaborative Hardware Problem Analysis
On the one hand, collaboration is critical, but, on the other hand, it comes with certain issues. The problem that may arise in the course of the work is the problematic or unclear communication patterns or the lack of congruency of objectives in a team. In this regard, it may be necessary to set up how the team will communicate to make a detour to thwart misunderstandings regarding the goals and objectives of the project.
Task 5
To document the plan for creating a high-end gaming PC, particularly focusing on the troubleshooting processes, you can incorporate the CompTIA A+ troubleshooting methodology and best practices as outlined in Module 1, Topic 1.6. Here's how you can structure this section:
Task 5: High-End Gaming PC Build Plan
Objective
The goal is to design and document a high-end gaming PC build capable of handling 4K gaming, virtual reality (VR), and multitasking efficiently. The target budget ranges from $2,000 to $3,500, aiming to maximize performance and future-proof the system.
Component Selection
Here's a detailed breakdown of the chosen components:
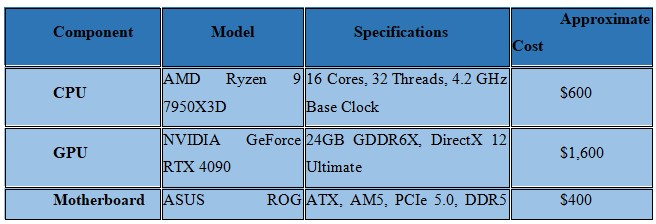
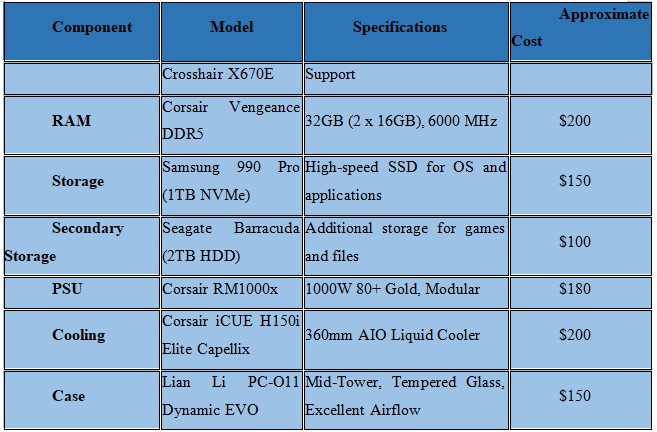
Assembly Plan
1. Preparation:
- Keep environment free from dust and other interfere with electrical conductivity.
- Prepare all that is required: screwdrivers, an anti-static wristband.
2. Component Installation:
- Motherboard: First, you must fit the CPU to the MOB, DM, and NutX boots with RAM, and NVMe SSD. Screw the motherboard into the case and fit it back in place.
- Cooling: Connect the AIO liquid cooler to the CPU and also ensure that the radiator is positioned correctly in the case.
- GPU: Take the GPU fit it into the PCIe slot of the motherboard and lock it into place.
- Power Supply: Mount the PSU in the case and secure its cables to the ATX, GPU and storage compartments of the motherboard.
- Storage: Screw the SSD and the HDD in the right positions, their bays in the computer case.
3.Cable Management:
- Install cables in a neat manner and in a way that will allow proper ventilation and cable management.
- Implement cable management for cables to be fastened by cable ties so that those cables do not come in contact with the fans.
4.Testing and Verification:
- Boot the system and go to the BIOS setting to confirm all the functional chains of the components.
- Configure the operating system (for instance Windows 11) and related drivers.
o Check system stability and its performance against a specific baseline by running stress tests and benchmarks.
Documentation
- Component List & Costs: Document each component where it is possible to get information on the model, the specifications, and the cost. It assists in some ways in monitoring expenditure and conformity.
- Build Log: Keep detailed records of every assembly process which include problems faced during the process and measures taken. The compilation of this log is useful in case you run into a problem with the instructions this log will help and it is helpful to refer to in future builds.
- Performance Metrics: Monitor the benchmarks and system temperature to try to establish its effectiveness and stability. Include graphics processing results originating from tools such as 3DMark or Cinebench.
- Maintenance Plan: Develop a list of various maintenance as well as activities like dusting that should be performed daily, weekly, monthly or at any specific intervals. This is very important in that it ensures that the PC is performing to the optimum when in use and also ensures longevity (Hackman & Warnow-Blewett, 1987).
Are you struggling to keep up with the demands of your academic journey? Don't worry, we've got your back!
Exam Question Bank is your trusted partner in achieving academic excellence for all kind of technical and non-technical subjects. Our comprehensive range of academic services is designed to cater to students at every level. Whether you're a high school student, a college undergraduate, or pursuing advanced studies, we have the expertise and resources to support you.
To connect with expert and ask your query click here Exam Question Bank

