Security Risk Assessment of Learning Management Systems Using CORAS Methodology CYBR7045
- Subject Code :
CYBR7045
1. Purpose/Rationale
The purpose of this assessment is to apply the CORAS methodology to a comprehensive risk evaluation of the Learning Management System (LMS). The CORAS method works especially well for security risk assessments because it provides a structured framework for figuring out, modelling, and handling potential threats. As educational institutions more and more rely on online learning systems, it is essential to become cognizant of the risks with the LMS so that these risks can be mitigated, in turn giving education its integrity and offering safe management of the users' data. Having referred to the CORAS methodology, this report will take into consideration the systematic evaluation of risks to support an informed decision related to the treatment of risks and, ultimately, the overall security posture of the LMS (Thiem et al., 2022). The actual result would be to continue using the platform efficiently and with thetrust of all users.
2. Scope and Focus of the Risk Assessment
2.1 Scope
The scope of this risk evaluation covers the security concerns associated with the Learning Management System (LMS), along with its components, subsystems, interfaces, and capability security troubles that can stand up. The assessment will consciousness on factors a the following traits.
Components: The LMS system has vital components including internet servers, which host the system and provide content material to the users; student and instructor entrances, supplying smooth access to instructional materials; administrative backends, coping with user accounts and course approvals; and third party equipment that improve productivity, such as cloud storage services and video conferencing platforms (Abdymanapov et al., 2021).
Subsystems: It will critically examine the diverse interaction of the user types in school; that is, students, instructors, and administrators, and how these groups might access and use the LMS (Alhazmi et al., 2021). Understanding these interactions will help identify specific vulnerabilities distinctive to each user type because they have varied needs and their access levels differ.
Interconnections: The LMS will work effectively only if there are links with other external tools and services. These links include linking integration with the cloud storage, to offer more space for other data, link integration with external educational resources to enrich the content of the student's learning in the LMS, and video conference solutions to provide the possibility to hold live sessions (Lai et al., 2024). Looking into these relationships will help to define risks coming from dependency on third-party services.
2.2 Focus
The main focus of the assessment is to ensure the safety of the LMS, especially in 3 main regions:
Confidentially: Ensuring that sensitive information, including educational and private records, remains inaccessible to unauthorized people is crucial. Thus, setting up robust authentication and access controls against even statistics breaches and ensuring only approved clients can view or manipulate sensitive information ensures such records.
Integrity: The assessment will point to the need for ensuring the accuracy and reliability of the records of information filed and dispensed in the LMS (Ismail et al., 2021). Procedures must be in place for identifying and preventing unauthorized access to the instructional substances, consumer profiles, and assessment results.
Availability: The other challenge would be the LMS has to be able to ensure users get access without disruption, especially at some point of peak periods that include tests and submission of assignments. That would involve testing the device for its resilience against cyberattacks, hardware disasters, and other capability disruptions that could render personal access impeded.
3. Target of the Risk Assessment
3.1 Goals of Analysis
The primary goal of this risk assessment is to become aware ofand examine potential dangers to the Learning Management System (LMS). This process starts offevolved with a scientific evaluation of dangers that would compromise system safety and overall performance, such as inner and external threats. Understanding these risks is important to developing effective techniques for developing LMS protection (Widodo et al., 2022). After the possible threats have been identified, the risk assessment will calculate the probability of each one of the threats happening, coupled with thepotential impact that the event may have on the LMS. This is an essential step in the prioritization of risks on the basis of the degree of severity and urgency level required in mitigating it. Understanding the likelihood and consequence of those threats makes it possible to focus available resources on risking the highest importance threats. The evaluation following the threat evaluation aimed to suggest tailored risk management strategies to mitigate the recognized dangers (Al-Sulami et al., 2023). These techniques can include technical measures together with enforcing firewalls and encryption, increasing consumer education to locate phishing tries, or reviewing coverage with strategies that address LMS capabilities via proactive measures, an organisation can notably reduce the LMS's vulnerability to capability threats.
3.2 Business Viewpoint
From the organization's perspective, an LMS is a vital tool for supplying instructional content material and facilitating communication among students and institutions. Monitoring the security and functionality of the LMS is crucial to non-stop productivity, as it permits academic activities to remain uninterrupted. Any downtime or breach of security can critically impede academic progress and harm the recognition of the institution. In addition, building trust among customers is of extreme importance; Students and instructors need to feel assured that their information is secure (Alomari et al., 2020). Compliance with prison and institutional regulations on records safety and privacy is likewise critical because it not only protects the business enterprise from legal outcomes, but additionally reinforces its commitment to ethical standards in education.
4. CORAS Asset Diagram
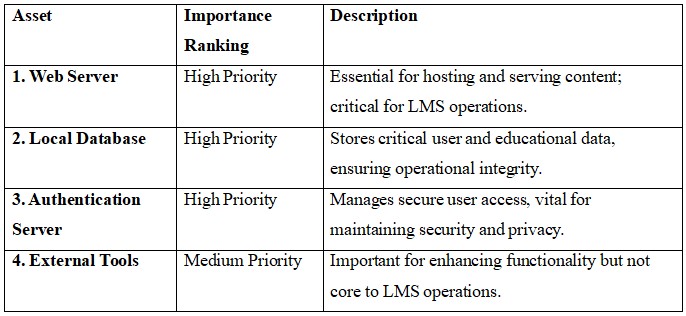
4.1 Asset Identification
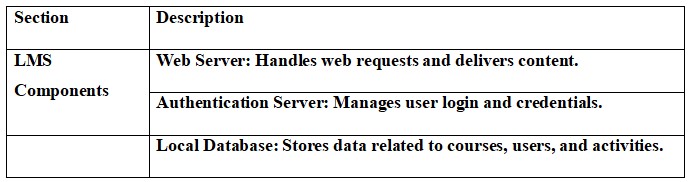
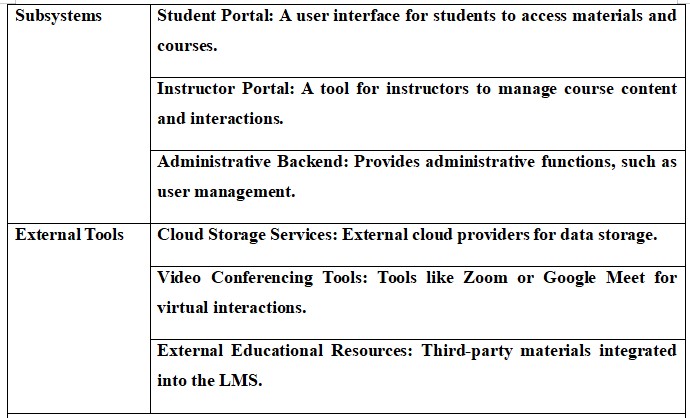
4.2 Asset Diagram
Fig: Asset Diagram
(Source: ResearchGate 2016)
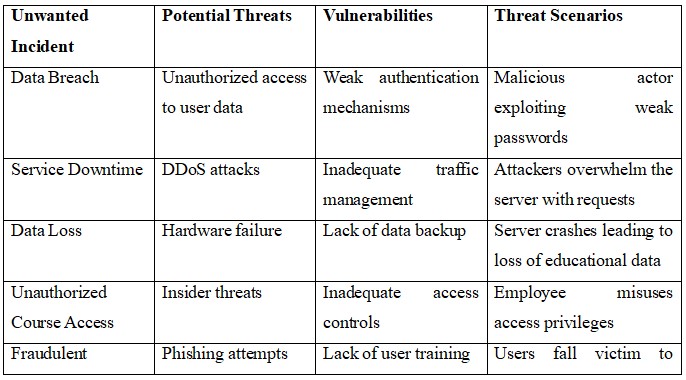
4.3 Unwanted Incidents, Threats, Vulnerabilities, and Threat Scenarios

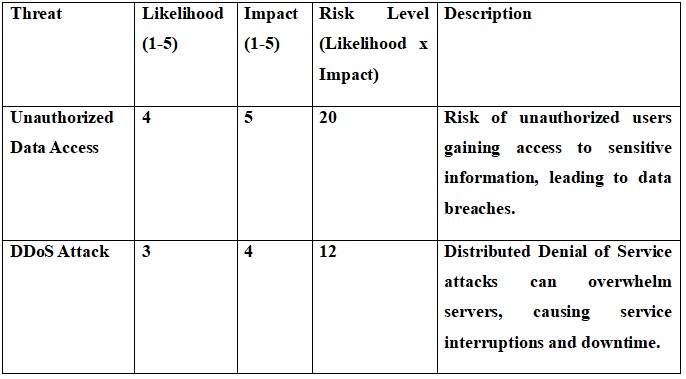
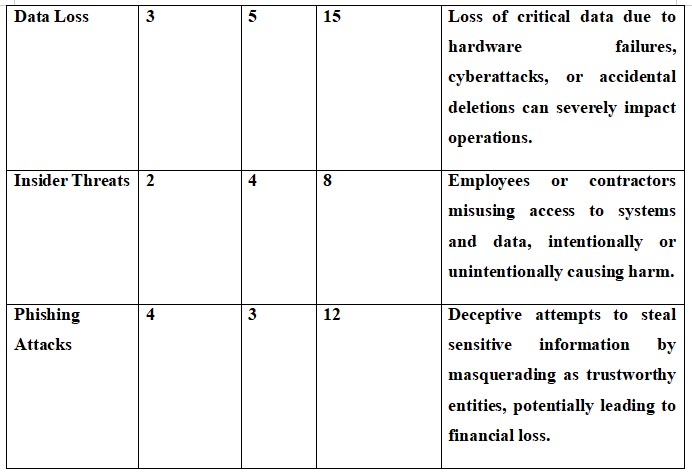
4.4 Asset Ranking and Risk Evaluation Metrics
Risk Evaluation Metrics:
Likelihood: Probability of a threat occurring (1-5 scale).
Impact: Severity of the consequence if a threat materializes (1-5 scale).
Risk Level: Overall risk calculated by multiplying likelihood and impact scores.
5. CORAS Threat Diagram
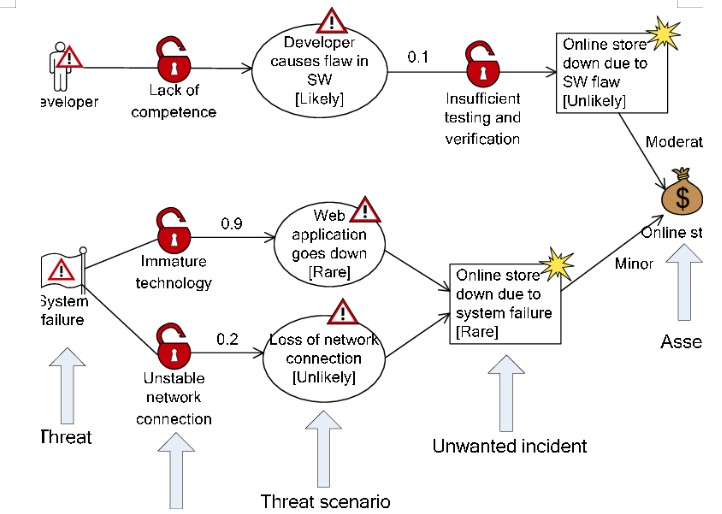
Fig: CORAS Threat Diagram
(Source: ResearchGate 2014)
5.1 Threat Identification
5.2 Threat Diagram

Figure: Threat Diagram
(Source: Self-developed)
6. CORAS Risk Treatment Diagram
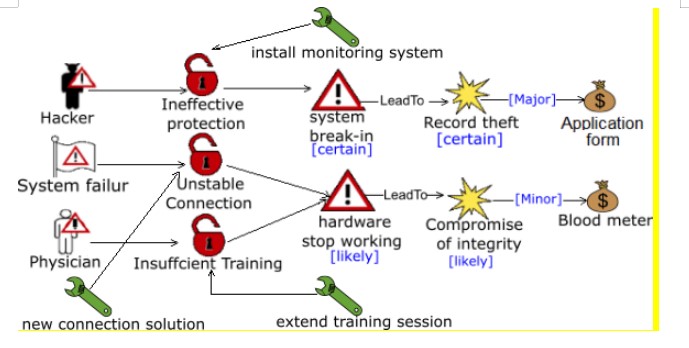
Fig: CORAS Risk Treatment Diagram
(Source: ResearchGate 2017)
6.1 Risk Treatments
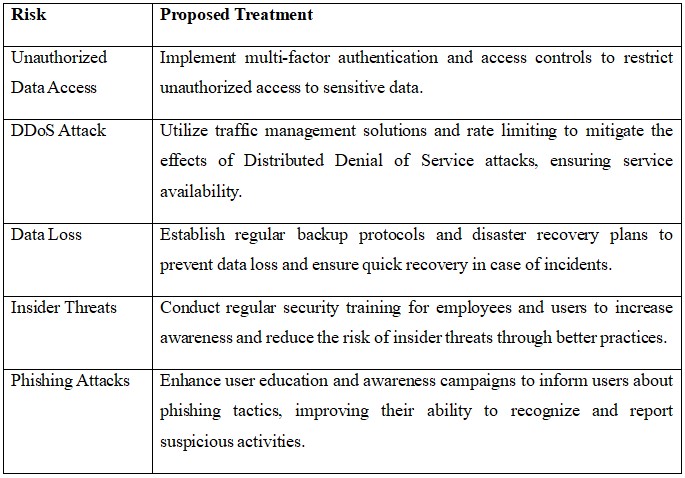
6.2 Risk Treatment Diagram
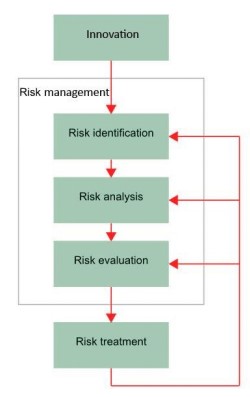
Fig: Risk Assessment Diagram
(Source: Self Developed)
7. Risk Evaluation and Acceptable Risks
Based on the threat diagram and proposed treatments, the following risks are evaluated for further action:
- Unauthorized Data Access: High risk that requires immediate attention due to its potential impact on user data confidentiality.
- Data Loss: Significant risk that must be addressed through backup protocols.
- Insider Threats: Moderate risk that can be mitigated through employee training.
- DDoS Attack and Phishing: While they pose risks, existing defenses can handle these effectively.
8. Conclusion
Using CORAS methodology, this risk assessment will precisely identify and model the several risks of theLearning Management System and come up with treatments for these identifiable risks. From the analysis of assets, potential threats, and relevant treatments in full mapping, it could point out several critical areas through which it can improve its posture towards security. It increases all aspects of confidentiality, integrity, and availability of educational data and therefore sets up a safe and dependable environment for both students and instructors. Furthermore, it is miles vital to recognize that the online education panorama is continuously evolving, with new threats emerging on a regular basis. Thus, continuous development and updating of this risk evaluation is crucial for theextra green edition. By being proactive and vigilant, a business enterprise can protect its LMS from potential vulnerabilities, ensuring a sturdy framework for online learning atthe same time as supporting instructional targets and trust.
Are you struggling to keep up with the demands of your academic journey? Don't worry, we've got your back!
Exam Question Bank is your trusted partner in achieving academic excellence for all kind of technical and non-technical subjects. Our comprehensive range of academic services is designed to cater to students at every level. Whether you're a high school student, a college undergraduate, or pursuing advanced studies, we have the expertise and resources to support you.
To connect with expert and ask your query click here Exam Question Bank

