Ethical Challenges and Privacy Concerns in Data Analytics: Case Studies and K-Anonymity Evaluation
Introduction
This report emphasizes the steps taken in the current report to examine the ethical pitfalls and violation of privacy in data analytics by analyzing two cases and a dataset. In the first case, a consultant is torn between ethical choices about how to recommend an appropriate IT security solution, and in the second, the ethical considerations of employing obscure algorithms and big data sources to decide which credits to approve. The report also involves the measurement of the same set of datasets using k-anonymity, which is a privacy metric. Lastly, it discusses how these cases have contributed to grappling with ethical dilemmas in the business analytics context.
Task 1
a) Impact on Data Privacy and Ethics
Essentials of the decision made by the CTO and the IT Manager to adopt a less secure solution bring into light data privacy and ethical issues in the implementation of this perspective based on the provisions of the Australian Privacy Act of 1988 and on the Code of Ethics of the ACS (Australian Computer Society, 2014, 2022).
According to the Privacy Act, entities are required to protect personal information from acts of unauthorized use, disclosure, interference, modification, or loss (Privacy Act 1988, F2021). Developing a lower-security product weakens the companys security, thus violating this out-of-sight, out-of-mind principle. It would mean that confidential details of employees and/or customers, including financial data, may be disclosed to individuals who do not have the right to access such information, be it insiders and/or external threats.
According to the ACS Code of Ethics, computing professionals have a responsibility whereby they must, if the workplace demands it, ensure that they have competence for the tasks they undertake and will act under this Code of Ethics and abide by other published standards of practice and procedures guiding their conduct (Australian Computer Society, 2014, p.2). Since the CTO and the IT Manager ignored Chelseas expert advice and went on to apply a faulty security solution, they have not complied with this ethical duty. They choose to spend as little as they can, and in so doing compromise the privacy of important data.
2). Since the CTO and the IT Manager ignored Chelseas expert advice and went on to apply a faulty security solution, they have not complied with this ethical duty. They choose to spend as little as they can, and in so doing compromise the privacy of important data.
Moreover, as part of the professional code of ethics, the ACS Code of Professional Conduct states that one should provide full and accurate assessments of criteria and potential options for action to a client or employer (Australian Computer Society, 2022, p. 3). Chelsea was able to do this duty by outlining the security threats and the recommended action to take in case of such a threat. However, the clients decision can be considered counter to the content of this principle, as the client chose an option that Chelsea had pointed out as unfavorable.
b) Recommendations for Chelsea
Based on the ethical concerns and possible legal issues that Chelsea may encounter, the candidate should not accept the introduction of the proposed low-security solution. Continuing would lead her to become a party to the clients unethical decision while elevating the risk of exposure of important information. To address this, she should forward her earlier communications to the client where she dismissed her findings with security concerns and the clients response.
If the client still does not use the proper security measures despite knowing the consequences for her company, then Chelsea must take the issue to the management of the consulting firm she is affiliated with. It is then the policy of the firm to take the appropriate actions which in this case may be to cancel the project of working with Chelsea or transfer her to another project to avoid compromising the companys ethical standards.
Chelsea could also consider seeking legal advice on the matter and consider reporting the matter to the appropriate vendors or regulatory agencies. ACS's code of professional conduct clearly explains that members should not perform any unlawful or unethical business by selling software or services (ACS, 2022, p. 4). That being the case, while the principle may not apply directly in this scenario, the underlying idea conveys the idea of escalating levels of unethical behavior that endangers public interests.
Finally, Chelsea has a responsibility to uphold the standards of her profession and safeguard the best interests of profiting subjects. The management of such risks would violate this duty and erode market trust in the consulting industry.
c) K-Anonymity Evaluation
It reveals that for the given quasi-identifiers {Sex, Age, Postcode} and the sensitive attribute Income, the concept of anonymity in the data taxonomic structure at different levels is as follows: It is not 2-anonymous, 3-anonymous, 4-anonymous, 5-anonymous, or 6-anonymous; but 1-anonymous.
For an obfuscation to have k-anonymity, then for any set of attributes quasi-identifiers in the table, every unique value or set of k-1 values must have at least k records (El Emam & Arbuckle, 2013). For a concise or increased protection level, each category of attributes: Sex, Age, and Postcode should not predict the record uniquely and each unique combination of the latter should have at least 2 records in the minimized dataset. However, as it can be noticed from the table, more than four combinations appear only once such as {male, 40-45, 318*} and {female, 30-35, 318*}.
Table: Dataset with Quasi-Identifiers and Sensitive Attribute
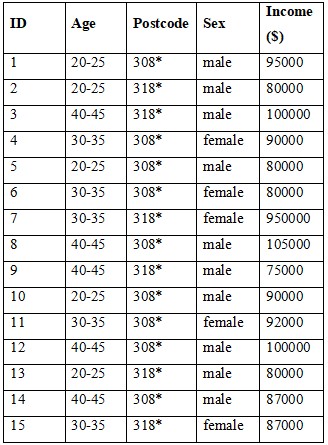
Consequently, the presented dataset does not meet the requirements for achieving 2-anonymity or a higher degree. Still, it is 1-anonymous because there are no two instances in the same table that have the same set of values of quasi-identifiers (El Emam & Arbuckle, 2013). The current level of anonymity might not be enough to preserve privacy due to circumstances where an attacker has prior knowledge of the specifics and can establish relationships with single records.
Task 2
a) Ethically Significant Harms
John and Hillary have potentially suffered several ethically significant harms due to the opaque loan evaluation process:
1. Lack of due process and accountability: Failure to grant the loan, offer any reasons why the application has been declined, and failing to allow the clients to appeal the decision are the major causes of procedural injustice according to Khan et al., 2022. John and Hillary have been denied the right of citizenship that embraced their right to know and reason in the decision-making making as well as contend the result in this case, which makes them lose their autonomy and dignity.
2. Discrimination and unfair treatment: (DATA COLLECTION) The employment of data sources and inferences that bear no relevance to creditworthiness like the race and medical history of the borrowers is considered prejudicial and unjust (Barocas & Selbst, 2016). Some of the possibilities include the fact that the system can be unfair to specific groups of people, due to letting in certain prejudices from the society to affect its decision-making process and deliver injustice based on such prejudice.
3. Invasion of privacy: The right to gather and use explicit data involving medical predispositions and individual choices involves a severe trespass on privacy (Nissenbaum 2004). John and Hillary have been caught unaware and have had their reasonable expectation of privacy breached in a manner that may have cumulative psychological effects and result in the loss of their trust in institutions.
These are all key aspects of John and Hillarys well-being financial, independence, and respect and are thus all viewed as important by most reasonable people. The inefficiency of disclosure and decision-making on matters concerning loans has deprived them of a deserved chance to realize their dreams of being entrepreneurs and not being offered fairness when it comes to the decision-making process.
b) Measures to Prevent Harms
To mitigate the ethically significant harms identified in the previous section, several measures and best practices should be implemented:
1. Transparency and explainability: The bank should explain itself in simple and understandable language for the loan decision; for instance, explain raw details showing as to where and from whom the gathered details were obtained, and the parameters used to arrive at that decision. One could argue that this transparency would make people understand why certain decisions were made and if it was RIGHT, then it is okay; this would hold decision-makers accountable.
2. Human oversight and appeals process: Loans especially those produced by automated processes and specifically by opaque algorithms should be reviewed and checked occasionally by human beings (Khan et al., 2022). Appeals process to allow those affected to challenge the decision and provide new reasons, circumstances, or information. This measure would help in strengthening the doctrine of due process of the law in cases. Hence, the measure would make lawyers accountable in case they abuse the legal process.
3. Data minimization and purpose limitation: The bank should collect only the data that is relevant and required for credit scoring, and follow the principles set by Nissenbaum (2004) on data minimization and purpose limitation. The loan approval should not be based on data that are either unrelated or sensitive and personal, like medical history or a consumers preferences, to avoid infringement on privacy and discrimination.
4. Algorithmic audits and impact assessments: It is also imperative that the algorithms used in loan evaluation be audited and undergo impact assessments regularly to check for fairness, and accuracy, and uncover possible bias. These assessments should incorporate reviews from not only domain specialists but also ethicists and representatives of the target community to garner a holistic understanding of how the system will impact these aspects.
5. Ethical governance and oversight: For the discussed potential issues, the bank should create an effective system of ethical governance that would control the development and application of algorithmic decision-making systems, so an ethical review board or an ethical committee could help with this task (Khan et al., 2022). With this structure of governance, it would be possible to ensure that the ethical issues are included in all the processes of designing and deploying these systems.
Although these measures could reduce the type and severity of harm as indicated above, they may not be easy to implement. For instance, making accurate and understandable foundational explanations for complicated machine-learning models sometimes can be technically demanding (Selbst & Barocas, 2018). Further, there could be resistance from the organizations to adopt solutions that may reduce their chances or opportunity to use the data or create the perception of a disadvantage to competitors.
Addressing these issues will imply coordinated actions by the national and supranational authorities, commercial actors, and civil society to introduce the existing principles of legal regulation, norms, and ethical standards to protect the society from negative consequences of algorithmic decisions. Further discussions and awareness-raising of ethical issues that can occur with the help of these innovations will also help to make people more aware of them.
Task 3: Reflection on Ethical Understanding
The case studies outlined, and the analysis carried out in this report have informed me in a very profound manner regarding the ethical questions in business analytics. In my experience, the first point of view was from the technical angle where innovation was embodied in elements like the quality of data, the performance of the model, or even the computers processing time. Of course, these aspects play a large role, but the few instances described in the cases point to highly significant ethical concerns related to the application or abuse of data analysis.
The first case study thus opened my eyes to how organizations would consider higher costs worthy in the instance of data security and privacy. The managements decision made by the CTO and the IT Manager to implement an inadequate security solution testifies to the fact that the large-scale use of powerful, yet affordable hacking tools can lead to ethical failures, driven by the mentality of short-term benefits. This case also provided an understanding concerning professional ethical principles and applying them while being ready to stand for an unfavorable decision influencing the client.
The second case study provided new ethical dilemmas on algorithmic decision making specifically discrimination, no procedural fairness or due process, and privacy violations. Before this, I never bothered with the possibility of the existence of negative possibilities that those mysterious systems may bring due to the usage of sensitive or irrelevant data. This case brought to light some of the important factors that should not be overlooked when it comes to the application of such systems including Accountability, Ethical governance, and disclosure.
Combined, these cases shaped my understanding of the expectations placed on me as a professional who is to maintain ethical integrity of the business analytics field. With this, I have realized how highly valuable data can be in the lives of individuals and how a data-driven society is beginning to function. Taking this into consideration, as a professional in this field, I have the following responsibilities: technical responsibility for projects that I complete and ethical responsibility for their ethical nuances that I address and consider.
This responsibility requires the ability to assess the data and the assumptions and possible biases in the data sources, the algorithms used to process the data, and the position of championing more robust fair, and accountable analytical systems. It also means being prepared to speak up ethically and to state no to undertaking activities or interfering in actions that are ethically unsound despite pressure from the organization or the client.
In addition, there is a need for constant ethical education, as well as updating the knowledge of new ethical dilemmas and ethically sound recommendations for the field of data analytics. To these points, we can add new ethical concerns that emerge whenever the applied technologies begin to expand their applications: whenever their capabilities increase, new forms of ethical dilemmas arise, which can be solved only through continuous involvement and refining of professional ethical norms.
Conclusion
Consequently, the cases outlined in this report have greatly nourished my comprehension of the aspects of ethical issues within business analytics. This is because they have debunked my initial concepts about ethics, raised new ethical issues, and impacted my perspective when it comes to meeting and maintaining ethical practices in this profession. With this knowledge in mind, I strive to apply ethical thinking the best way that I can in my field of practice and be an active participant in the building of solutions for Data Analytics that are not only responsible but also trustworthy.
Are you struggling to keep up with the demands of your academic journey? Don't worry, we've got your back!
Exam Question Bank is your trusted partner in achieving academic excellence for all kind of technical and non-technical subjects. Our comprehensive range of academic services is designed to cater to students at every level. Whether you're a high school student, a college undergraduate, or pursuing advanced studies, we have the expertise and resources to support you.
To connect with expert and ask your query click here Exam Question Bank

